Connectusers Adobe Leak - 223 passwords in 2 seconds
 Sunday, November 18, 2012 at 7:06PM
Sunday, November 18, 2012 at 7:06PM As most of you already know there is word of a leak involving Adobe's Connectusers forum. You can read more about this at The HNN. The important things to know in relation to this post is that 642 hashes have been released so far and the attacker claims to have 150,000 more to share. The attacker also released other information with these hashes such as name, title, phone, email, company, and username.
What I have done with the release is first strip out the data I don't want leaveing me with just the hashes.
cat adobe-leaks.txt | grep Password | cut -d: -f 2 >adobehashes
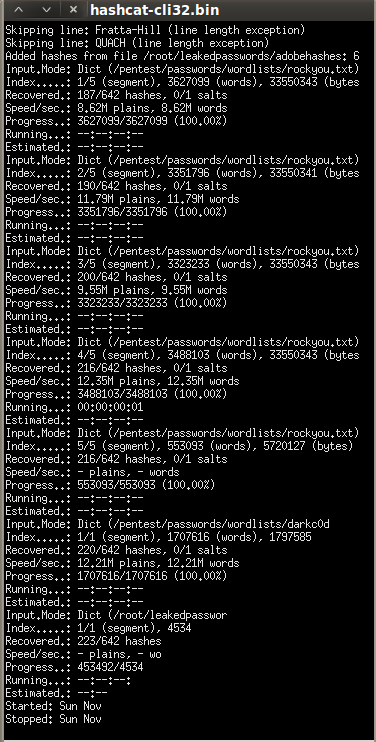
Now that I have a file with just the hashes, I ran hashcat against the hashes using a few wordlists.
root@bt:./hashcat-cli32.bin --output-file /root/leakedpasswords/ah3.out /root/leakedpasswords/adobehashes /pentest/passwords/wordlists/rockyou.txt /pentest/passwords/wordlists/darkc0de.lst /root/leakedpasswords/yahoopassesonly.txt
In less than 2 seconds, usin only those three wordlists I was able to extract 223 of the 642 passwords. I mention this because people who do not use these tools may not understand how fast and easy it can work.
Here is a small sampling of the hashes and passes:
a66edf0fea452ada254f5b9df1e06a37:3622125db3b81e16cc975d2edcc1c4acf36e895:35700849858a41a0d7d1d2e38b61513046403d:Daniel81b23e8ea5a3a6ba0bd3ba22630ee3f153:8biggtoes17120d69065bd6a1b6393c6e2db4174e:CDE#4rfvc21435496168ad21cc9ba0a8e5542ec8:C0nn3cta4f2a54552dc5f7e1fecb1a3e9c94a59:2more2goe20d81b83905638dbda34442b4703b4e:292520834e2d1989a1dbf75cd631596133ee5ee:Videod4a6f575e71a416ff8894c6baae0ccd9:48jjfan14dec073747d945943aaddc07a0d965e:Soccer_1491381b03056102fcfe5538f87721e144:@WSX4rfv6a4de56cfde1980ea9667ef3bfb77d54:9982d269508cbf2647fd5a5cb23fe3a524c8cc3:Heidi123cbbd41ba72c93d17f17f2a484295b221:40452655d7443eeb55ed7786fa89a2cc1bf446:Pass123Wordd4af0320ac68d2b8ad0f8e5faa5a1977:mdnite11a7a5d55a91adb201e113967eff93fe:collaboration826805d5bdaa87a3b9c7ead9027a3067:aftereffects71f698950c9cdadc3d19bb7411177a78:Adobe952f9dc3ad0b4c8f94de8ec75f8daeb3:trek930d05a718ceb3cc5c368cc166729c7c7cb:Tanner07f896dcdeb0ca7d797b439624b0e04ffe:inciner8
The full list can be downloaded here.
So, since I just did a TekTip episode on Pipal I figured I should run the output against there as well.
cat ah.out | cut -d: -f2 > ahpassesonly
./pipal.rb ~/leakedpasswords/ahpassesonly -o ahanalysis.txt
Total entries = 538Total unique entries = 223Top 10 passwordsletmein = 3 (0.56%)lighthouse = 3 (0.56%)fisher = 3 (0.56%)popper = 3 (0.56%)carefree = 3 (0.56%)stanley = 3 (0.56%)Video = 3 (0.56%)Winston = 3 (0.56%)louie = 3 (0.56%)manish = 3 (0.56%)Top 10 base wordsbuster = 6 (1.12%)adobe = 6 (1.12%)marina = 5 (0.93%)soccer = 5 (0.93%)connect = 5 (0.93%)jonathan = 3 (0.56%)video = 3 (0.56%)winston = 3 (0.56%)louie = 3 (0.56%)manish = 3 (0.56%)Password length (length ordered)5 = 29 (5.39%)6 = 174 (32.34%)7 = 130 (24.16%)8 = 128 (23.79%)9 = 45 (8.36%)10 = 21 (3.9%)11 = 5 (0.93%)12 = 3 (0.56%)13 = 3 (0.56%)Password length (count ordered)6 = 174 (32.34%)7 = 130 (24.16%)8 = 128 (23.79%)9 = 45 (8.36%)5 = 29 (5.39%)10 = 21 (3.9%)11 = 5 (0.93%)12 = 3 (0.56%)13 = 3 (0.56%)|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||000000000011111012345678901234One to six characters = 203 (37.73%)One to eight characters = 461 (85.69%)More than eight characters = 77 (14.31%)Only lowercase alpha = 302 (56.13%)Only uppercase alpha = 3 (0.56%)Only alpha = 305 (56.69%)Only numeric = 29 (5.39%)First capital last symbol = 2 (0.37%)First capital last number = 19 (3.53%)Monthsjune = 2 (0.37%)november = 2 (0.37%)DaysNone foundMonths (Abreviated)mar = 12 (2.23%)jun = 2 (0.37%)nov = 2 (0.37%)Days (Abreviated)mon = 5 (0.93%)sat = 2 (0.37%)sun = 2 (0.37%)Includes years1979 = 2 (0.37%)1989 = 2 (0.37%)2002 = 4 (0.74%)2007 = 2 (0.37%)Years (Top 10)2002 = 4 (0.74%)1979 = 2 (0.37%)1989 = 2 (0.37%)2007 = 2 (0.37%)Coloursorange = 2 (0.37%)red = 8 (1.49%)white = 3 (0.56%)Single digit on the end = 52 (9.67%)Two digits on the end = 57 (10.59%)Three digits on the end = 19 (3.53%)Last number0 = 11 (2.04%)1 = 45 (8.36%)2 = 16 (2.97%)3 = 24 (4.46%)4 = 6 (1.12%)5 = 14 (2.6%)6 = 13 (2.42%)7 = 11 (2.04%)8 = 13 (2.42%)9 = 14 (2.6%)|||||||| || || ||||||| || |||||| |||||||||||||||||||||||||||||||||||0123456789Last digit1 = 45 (8.36%)3 = 24 (4.46%)2 = 16 (2.97%)5 = 14 (2.6%)9 = 14 (2.6%)6 = 13 (2.42%)8 = 13 (2.42%)0 = 11 (2.04%)7 = 11 (2.04%)4 = 6 (1.12%)Last 2 digits (Top 10)23 = 16 (2.97%)99 = 6 (1.12%)12 = 6 (1.12%)08 = 6 (1.12%)25 = 6 (1.12%)56 = 5 (0.93%)13 = 4 (0.74%)14 = 4 (0.74%)66 = 4 (0.74%)02 = 4 (0.74%)Last 3 digits (Top 10)123 = 14 (2.6%)002 = 4 (0.74%)456 = 3 (0.56%)388 = 2 (0.37%)085 = 2 (0.37%)989 = 2 (0.37%)900 = 2 (0.37%)110 = 2 (0.37%)966 = 2 (0.37%)325 = 2 (0.37%)Last 4 digits (Top 10)2002 = 4 (0.74%)3456 = 3 (0.56%)2898 = 2 (0.37%)1085 = 2 (0.37%)1989 = 2 (0.37%)6900 = 2 (0.37%)6966 = 2 (0.37%)2325 = 2 (0.37%)3388 = 2 (0.37%)2007 = 2 (0.37%)Last 5 digits (Top 10)23456 = 3 (0.56%)12898 = 2 (0.37%)61085 = 2 (0.37%)26900 = 2 (0.37%)16966 = 2 (0.37%)52325 = 2 (0.37%)13388 = 2 (0.37%)52963 = 2 (0.37%)55225 = 2 (0.37%)11979 = 2 (0.37%)US Area Codes456 = Inbound International (--)989 = Upper central Michigan: Mt Pleasant, Saginaw (MI)900 = US toll calls -- prices vary with the number called (--)325 = Central Texas: Abilene, Sweetwater, Snyder, San Angelo (TX)Character setsloweralpha: 302 (56.13%)loweralphanum: 149 (27.7%)numeric: 29 (5.39%)mixedalphanum: 23 (4.28%)mixedalpha: 18 (3.35%)mixedalphaspecialnum: 12 (2.23%)upperalpha: 3 (0.56%)mixedalphaspecial: 2 (0.37%)Character set orderingallstring: 323 (60.04%)stringdigit: 132 (24.54%)alldigit: 29 (5.39%)stringdigitstring: 24 (4.46%)othermask: 18 (3.35%)digitstring: 6 (1.12%)stringspecial: 2 (0.37%)digitstringdigit: 2 (0.37%)stringspecialdigit: 2 (0.37%)Hashcat masks (Top 10)?l?l?l?l?l?l: 120 (22.3%)?l?l?l?l?l?l?l: 71 (13.2%)?l?l?l?l?l?l?l?l: 56 (10.41%)?l?l?l?l?l?l?d?d: 22 (4.09%)?l?l?l?l?l: 18 (3.35%)?l?l?l?l?l?l?l?l?l: 17 (3.16%)?d?d?d?d?d?d: 17 (3.16%)?l?l?l?l?l?l?l?d: 15 (2.79%)?l?l?l?l?l?d?d: 12 (2.23%)?l?l?l?l?l?l?l?l?l?l: 11 (2.04%)