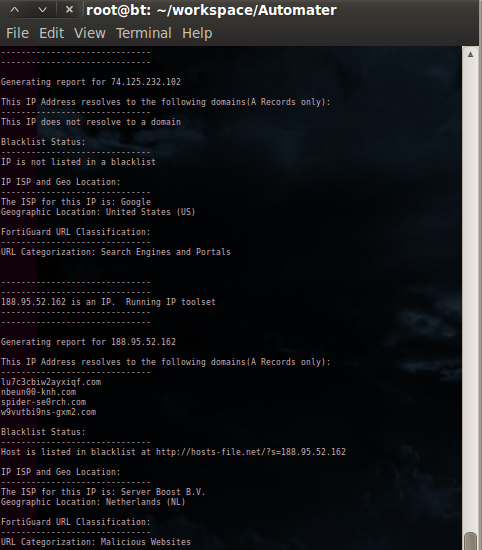
Automater added to Kali (The new BackTrack)
 Friday, March 22, 2013 at 9:20AM
Friday, March 22, 2013 at 9:20AM Update: Automater gets its own project page http://www.tekdefense.com/automater/
I must admit, I am in a bit of shock here. Never did I think I would actually get to have something I developed on the most popular distribution for security professionals. For those who do not know, Kali is the successor to Backtrack, this time fully debian based.
As of 2013/03/22 Automater was added to the Kali repos. What does that mean for you? If you are on Kali or have their repos added as a source you can now apt-get install automater.
Installation of automater on Kali:
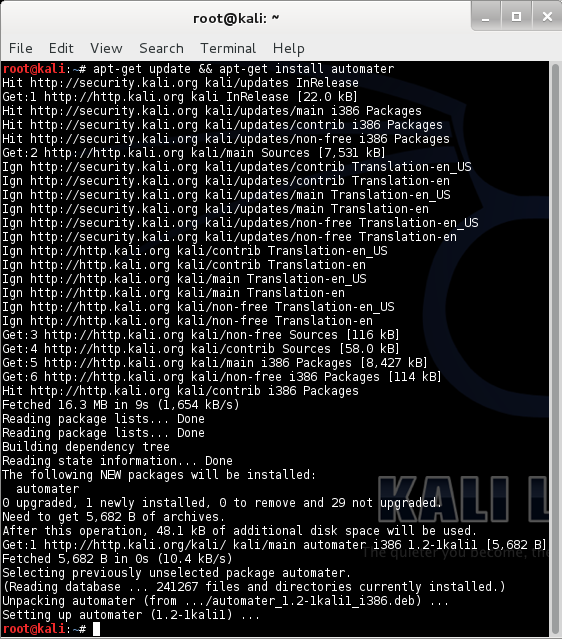
In order to ensure you are able to pull automater from Kali you must first update your repos. to do this simply:
apt-get update
Once updated you can install automater with the following command:
apt-get install automater
You can roll both of those commands into one if you like, as seen in the screenshot below.
It is that simple, installation complete. Of course if you are not on kali you can still grab the latest version of automater from Github.
Automater usage:
Once installed via apt-get, automater is placed in /usr/bin/ which is in the PATH. So you can run automater from any directory.
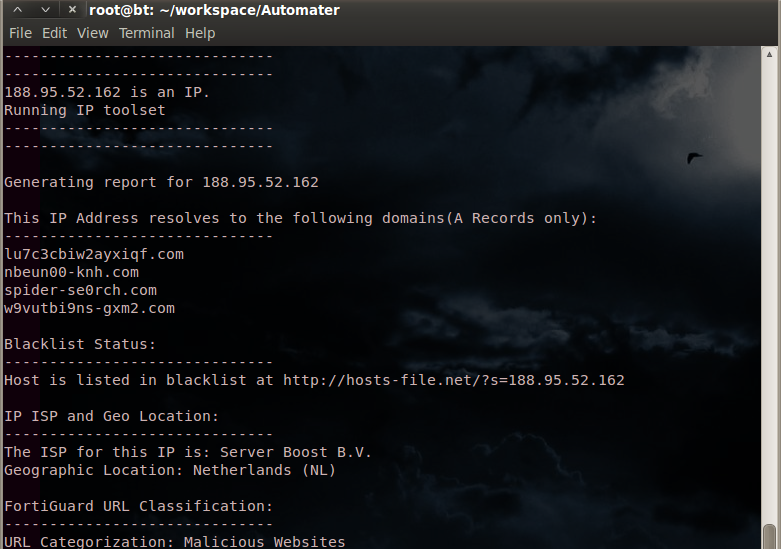
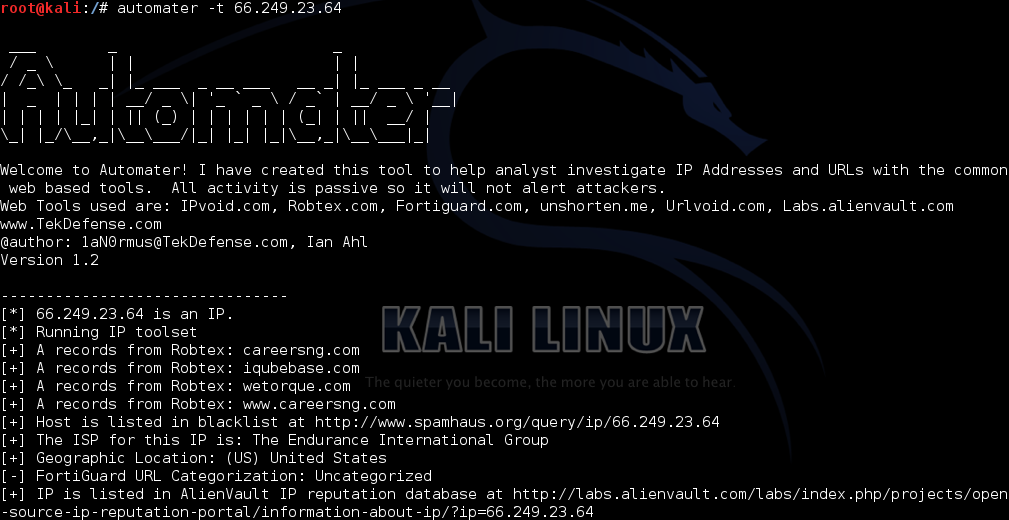
Single target is an ip:
automater -t 66.249.23.64
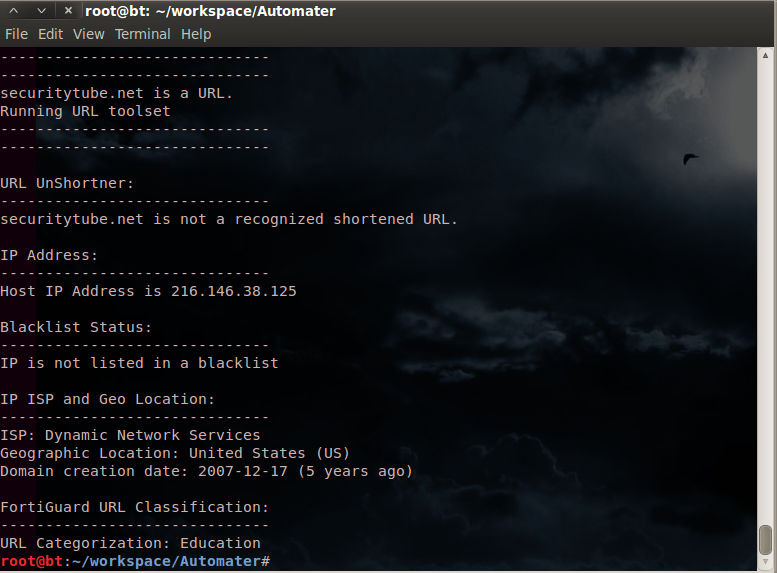
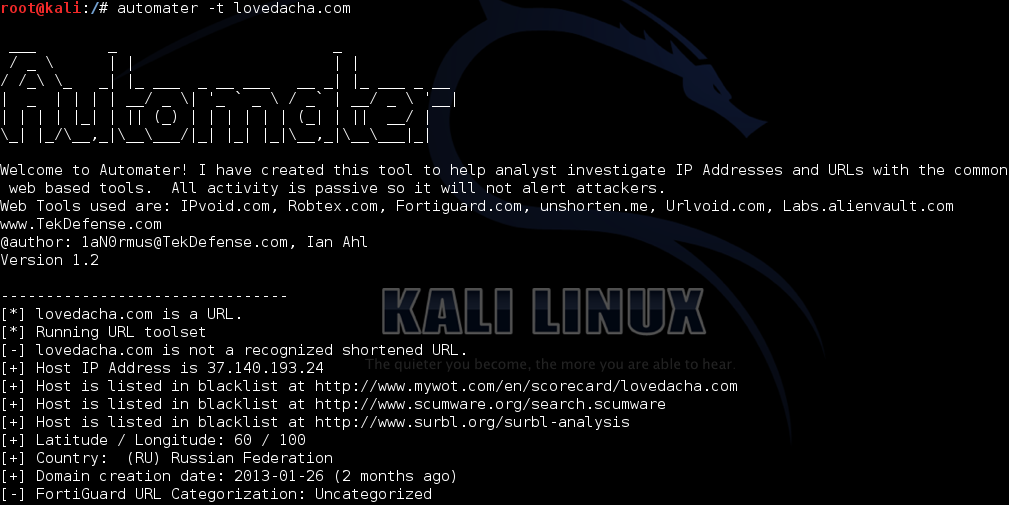
Single target is a url/domain:
automater -t lovedacha.com
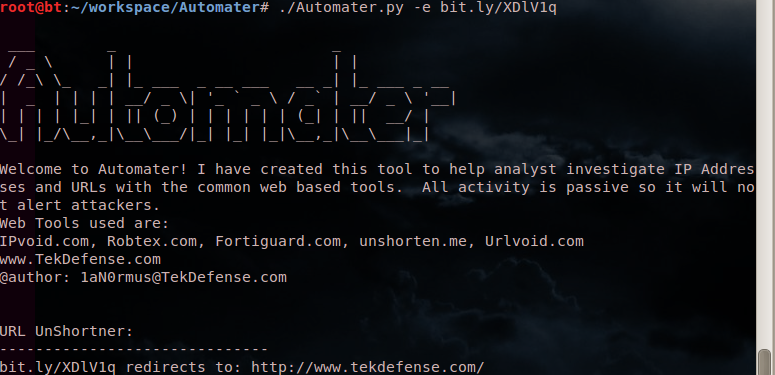
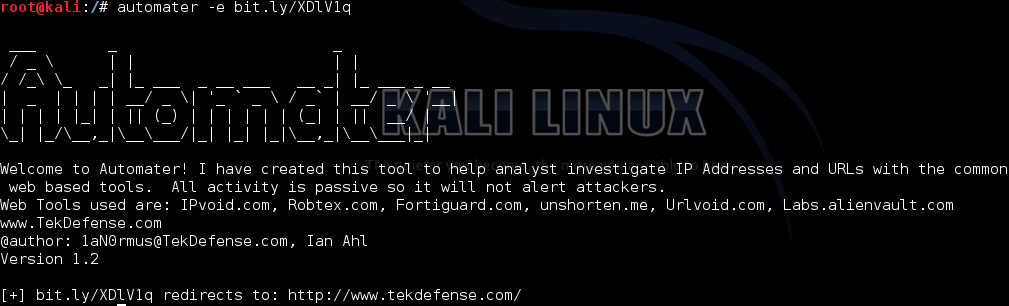
Single target is a shortened url:
automater -e bit.ly/XDlV1q
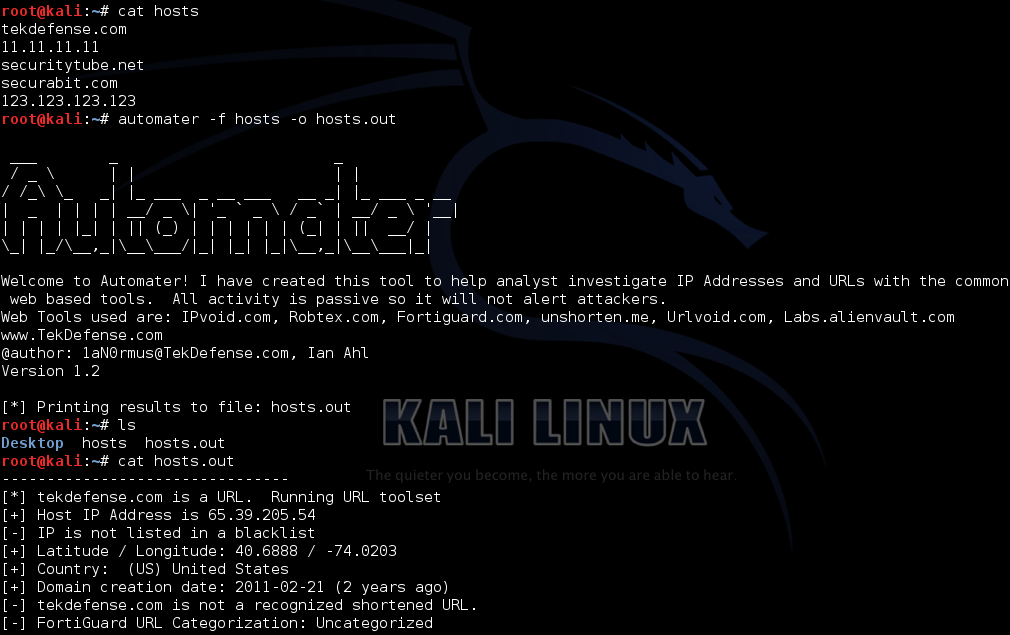
Target is several IPs and URLs/Domains listed in a file called hosts, outputting to another file called hosts.out:
automater -f hosts -o hosts.out
I have some really fun things planned for automater, such as adding a hash search function. I hope you enjoy.