Tektip ep26 - Information gathering with recon-ng
 Sunday, March 24, 2013 at 11:45AM
Sunday, March 24, 2013 at 11:45AM In this episode of TekTip, we focus on using @LanMaster53's reconnaissance framework recon-ng.
From his site:
"Recon-ng is a full-featured Web Reconnaissance framework written in Python. Complete with independent modules, database interaction, built in convenience functions, interactive help, and command completion, Recon-ng provides a powerful environment in which open source web-based reconnaissance can be conducted quickly and thoroughly."
To see some tips and tricks on usage and development using the framework goto the wiki.
Recon-ng is written entirely in python and is very modular. What this means is that it is that anyone with python experience can utilize the framework to develop their own modules. I will probably do a follow on episode where I go over developing a module for recon-ng.
Recon-ng already has a decent amount of modules already. At the time of me writing this there are already 59 modules released.
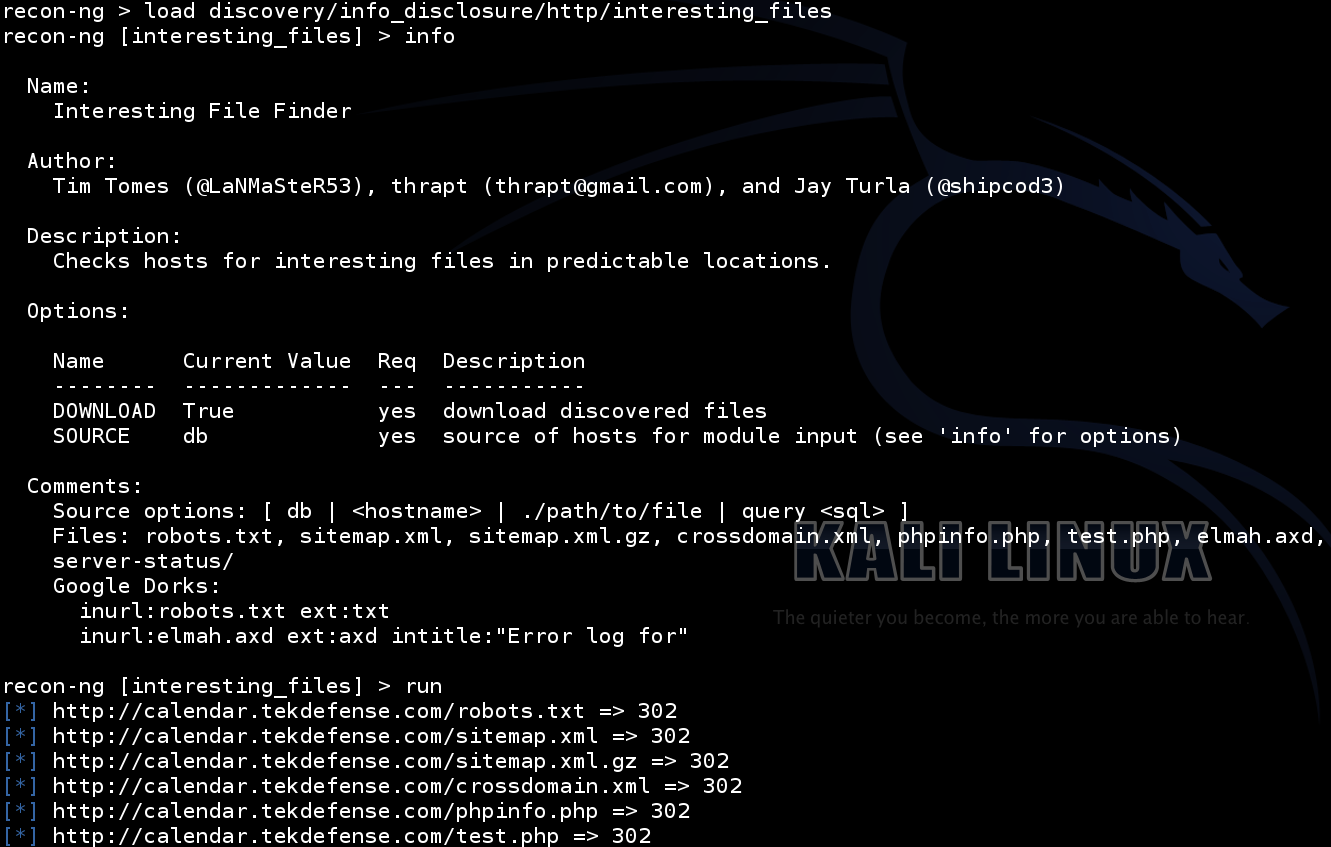
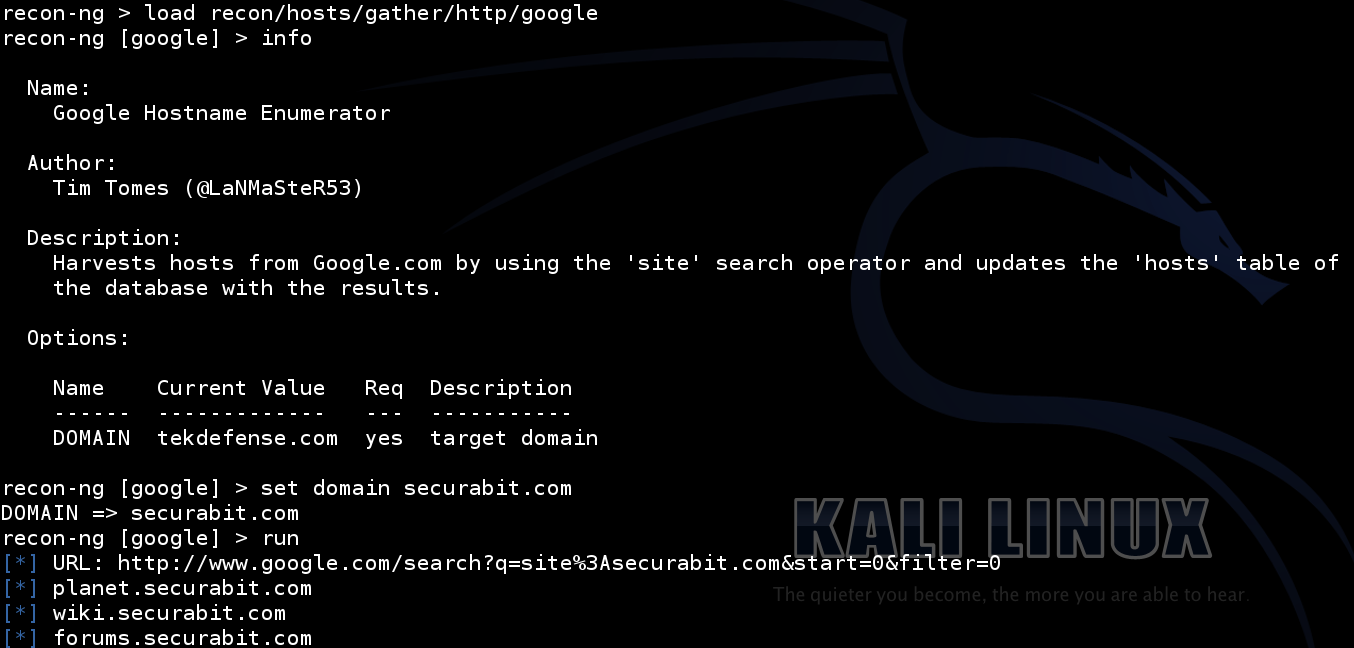
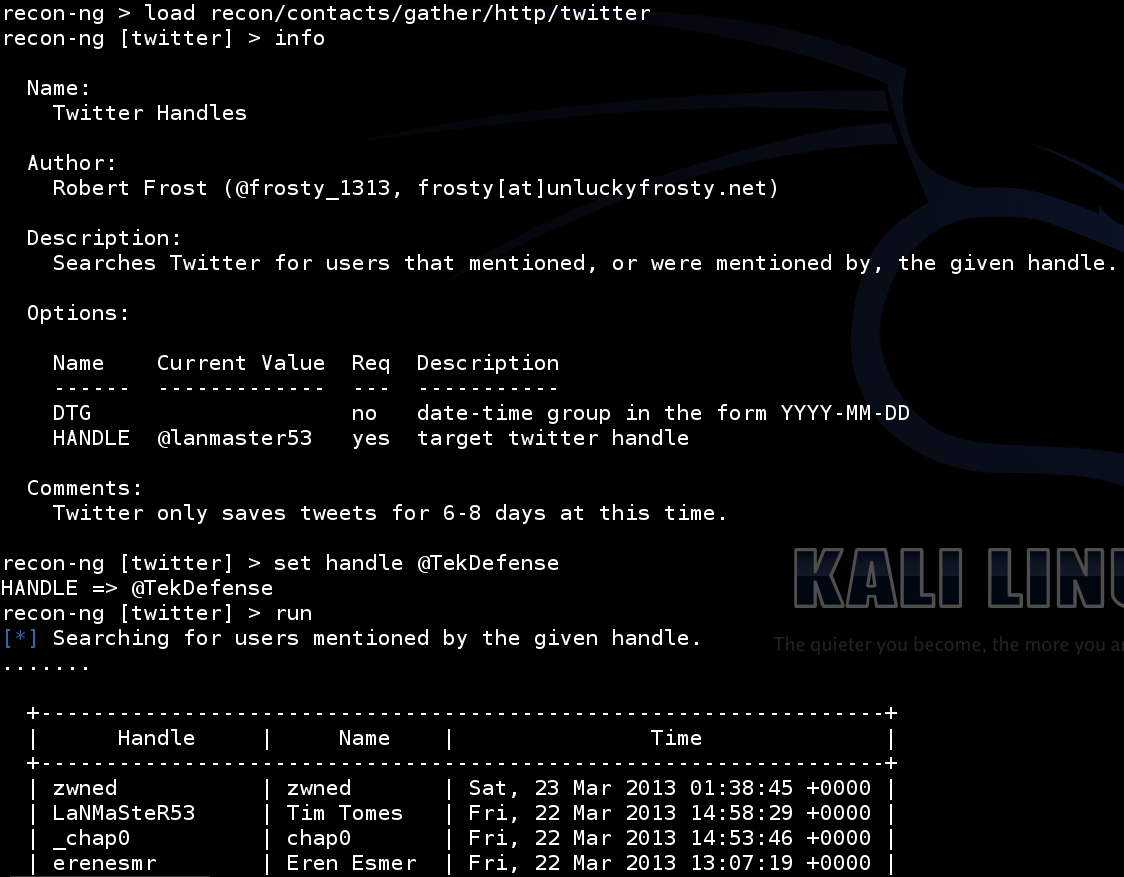
Running modules in recon-ng is very similar to the commands you would use in Metasploit. The following are a few example modules I ran in the video:
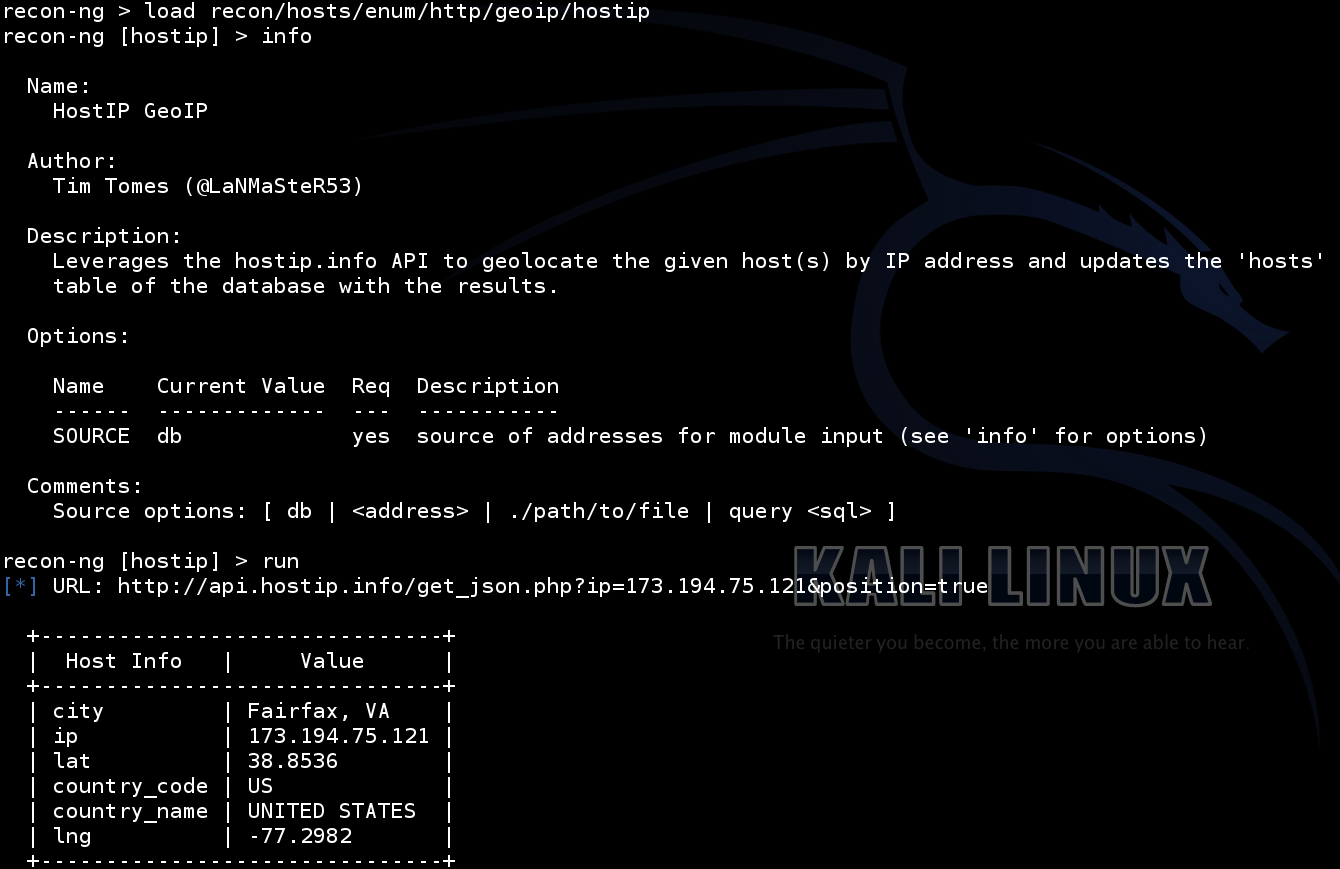
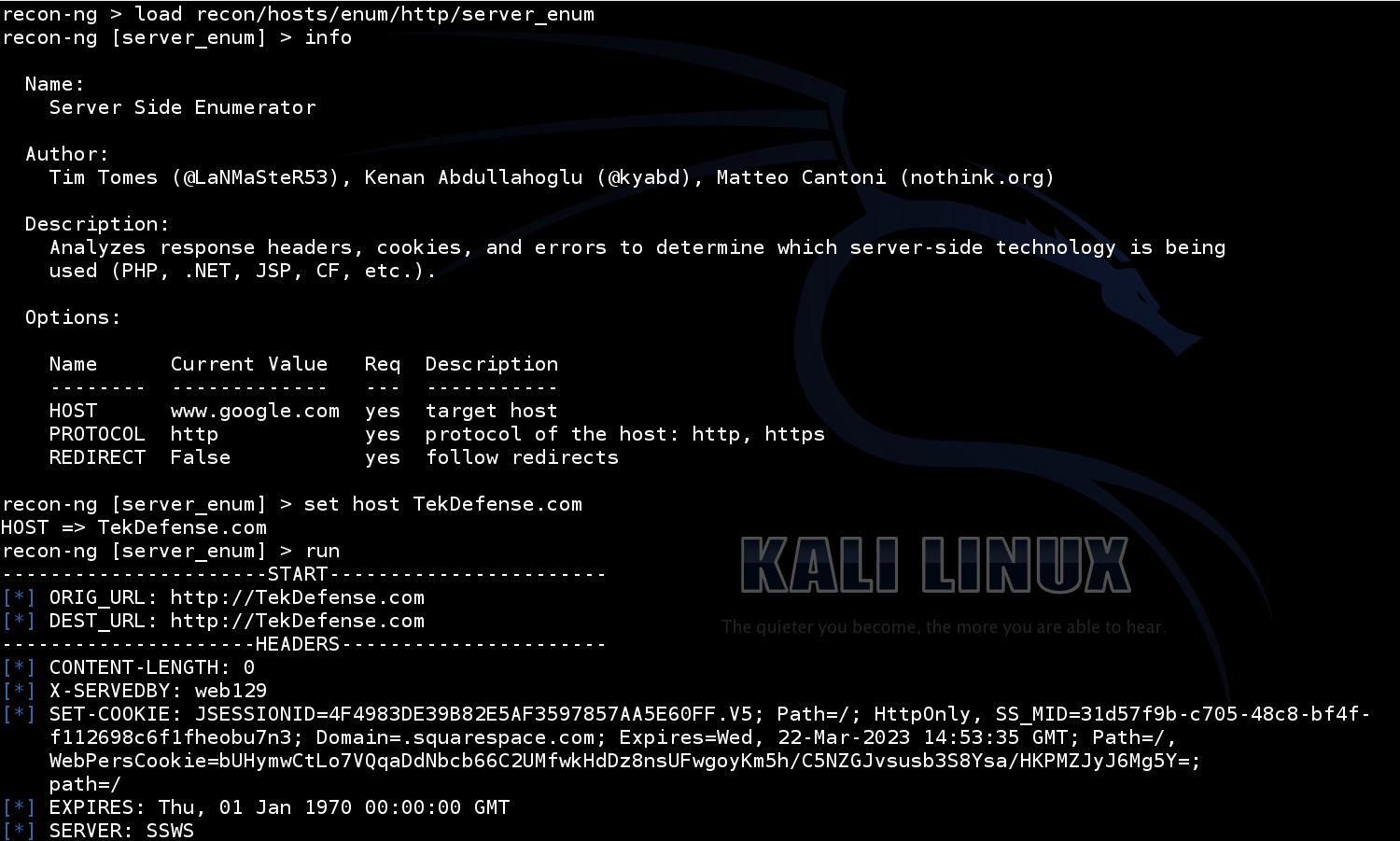
Once completed running the modules you want to run for recon, you may want to produce some sort of report. Here is an example of an http report that was generated with a reporting module.
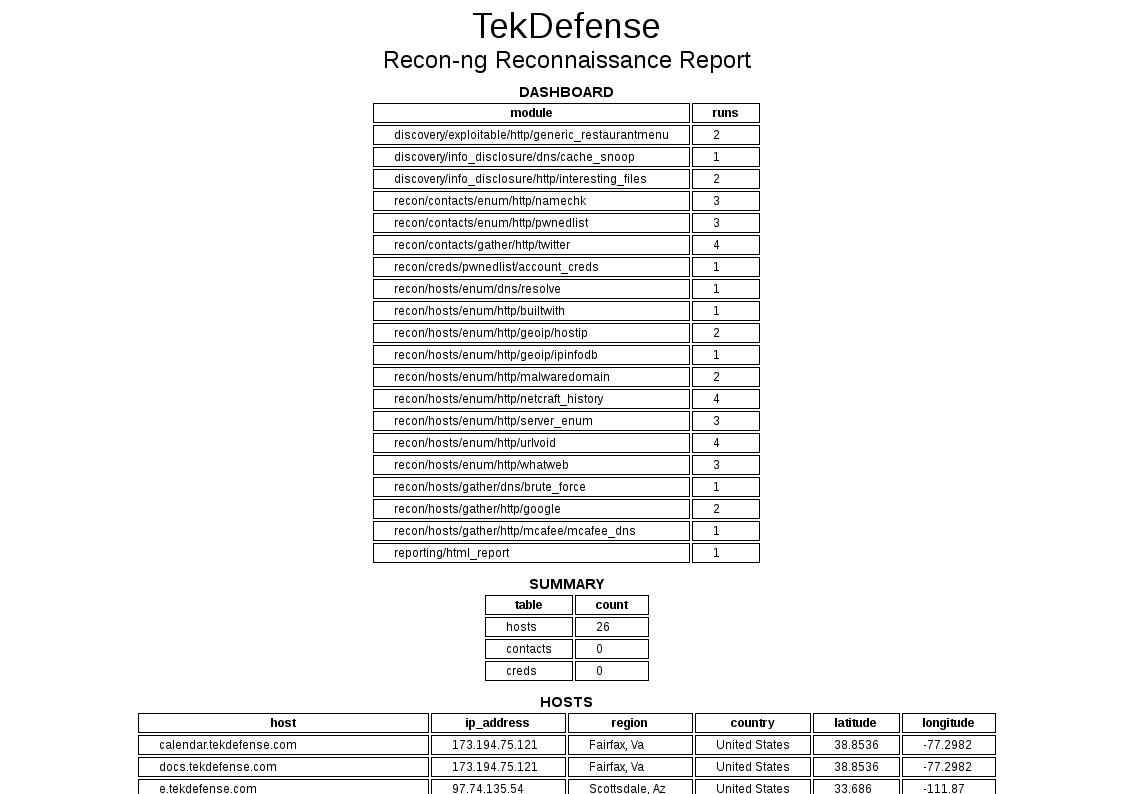
Overall, I think recon-ng is a great tool that shows a lot of promise. As the number of modules grows and as people share resource files I think the value will grow tremendously.
 Admin |
Admin |  Post a Comment |
Post a Comment |  information gathering,
information gathering,  passive,
passive,  python,
python,  recon-ng in
recon-ng in  News
News