Installing MASTIFF
 Sunday, March 10, 2013 at 2:09PM
Sunday, March 10, 2013 at 2:09PM So we have talked about using SecShoggoth 's MASTIFF (here, here, and here), but haven't really gone through the installation. Here goes...
I am assuming a base installation of Ubuntu 12.10 (because its easy and you can run it free on AWS). The first thing that we should do is update the base OS and install ssh for remote management.
sudo apt-get update; sudo apt-get upgrade -y; sudo apt-get dist-upgrade -y; sudo apt-get autoremove -y; sudo apt-get install openssh-server -y; sudo shutdown -r now later
Once that is back online we will begin installing the necessary packages for MASTIFF. I am running through the dependencies as they are introduced in the documentation. First lets get the python dependencies out of the way, as well as an editor (nano is fine...albeit evil)
sudo apt-get install python python-dev python-magic python-sqlite python-setuptools python-pip build-essential vim -y
Install yapsy from pip
sudo pip install yapsy
sudo chown -R `whoami`:`groups | awk '{print $1}'` /opt
cd /optmkdir /opt/tridcd /opt/tridwget wget http://mark0.net/download/trid_linux.zipunzip trid_linux.ziprm -f unzip trid_linux.zipchmod +x tridwget http://goo.gl/RQXV8unzip RQXV8rm -f RQXV8chmod +x tridupdate.pypython tridupdate.py
sudo aptitude install ia32-libs
sudo apt-get install subversion libpcre3 libpcre3-dev libpcre++-dev -ycd /opt/wget http://sourceforge.net/projects/ssdeep/files/ssdeep-2.9/ssdeep-2.9.tar.gztar -xvzf ssdeep-2.9.tar.gzrm -f ssdeep-2.9.tar.gzmv ssdeep-2.9 ssdeepcd /opt/ssdeep./configuremakesudo make installsudo ldconfigsvn checkout http://pyssdeep.googlecode.com/svn/trunk/ pyssdeepcd /opt/ssdeep/pyssdeeppython setup.py buildsudo python setup.py install
sudo apt-get install automake -ycd /optsvn checkout http://yara-project.googlecode.com/svn/trunk/ yaracd /opt/yarasudo ln -s /usr/bin/aclocal-1.11 /usr/bin/aclocal-1.12./configuremakesudo make installcd yara-pythonpython setup.py buildsudo python setup.py install
sudo apt-get install git -ycd /optgit clone https://github.com/simplejson/simplejson simplejsoncd /opt/simplejsonpython setup.py buildsudo python setup.py build install
mkdir /opt/pdftoolscd /opt/pdftoolswget http://didierstevens.com/files/software/pdf-parser_V0_3_9.zipunzip pdf-parser_V0_3_9.ziprm -f pdf-parser_V0_3_9.zipchmod +x pdf-parser.pywget http://didierstevens.com/files/software/pdfid_v0_0_12.zipunzip pdfid_v0_0_12.ziprm -f pdfid_v0_0_12.zipchmod +x pdfid.py
cd /optwget http://www.sno.phy.queensu.ca/~phil/exiftool/Image-ExifTool-9.22.tar.gztar -xvzf Image-ExifTool-9.22.tar.gzrm Image-ExifTool-9.22.tar.gzmv Image-ExifTool-9.22 exiftool
cd /optsvn checkout http://pefile.googlecode.com/svn/trunk/ pefilecd /opt/pefilepython setup.py buildsudo python setup.py build install
mkdir /opt/disitoolcd /opt/disitoolwget http://www.didierstevens.com/files/software/disitool_v0_3.zipunzip disitool_v0_3.ziprm disitool_v0_3.zip
sudo apt-get install openssl -y
mkdir /opt/pyOLEScannercd /opt/pyOLEScannerwget https://github.com/Evilcry/PythonScripts/raw/master/pyOLEScanner.zipunzip pyOLEScanner.ziprm pyOLEScanner.zipchmod +x pyOLEScanner.py
cd /optsvn checkout http://distorm.googlecode.com/svn/trunk/ distormcd /opt/distormpython setup.py buildsudo python setup.py build install
cd /optwget http://downloads.sourceforge.net/project/mastiff/mastiff/0.5.0/mastiff-0.5.0.tar.gztar -xvzf mastiff-0.5.0.tar.gzrm mastiff-0.5.0.tar.gzmv mastiff-0.5.0/ mastiffcd /opt/mastiffsudo make install
mkdir /etc/mastiffcd /etc/mastiffcat > /opt/mastiff/mastiff.conf.TEST <<EOF# This is the configuration file for mastiff.## Comments are preceded by a # or ;#[Dir]# log_dir is the base directory where the logs generated will# be placed in.#log_dir = /usr/local/mastiff/loglog_dir = ./work/log# plugin_dir is a list of directories plugins may be present in.# should be comma-separated.plugin_dir = ./plugins, /etc/mastiff[Misc]# verbose = [on|off]verbose = off[Sqlite]# Sqlite database options# db_file = Name of the database filedb_file = mastiff.db[File ID]# trid is the location of the TrID binary# trid_db is the location of the TrID database#trid = /usr/local/bin/tridtrid = /opt/trid/trid#trid_db = /usr/local/etc/triddefs.trdtrid_db = /opt/trid/triddefs.trd[Embedded Strings Plugin]# Options for the Embedded Strings Plugin.# strcmd is the path to the strings commandstrcmd = /usr/bin/strings[VirusTotal]# Options for the VirusTotal Submission Plug-in.# api_key is your API key from virustotal.com# - Leave this empty if you wish to disable this plug-inapi_key = GET_YOUR_OWN# submit [on|off] - submit binary to VirusTotalsubmit = off[pdfid]# Options to run Didier Stevens pdfid.py script# pdfid_cmd = Path to the pdfid.py script# - Leave blank if you want the script disabled.# pdfid_opts = Options for program.# - Do not put multiple options in quotes.# Note: pdfid.py has bugs that may cause errors when examining# malformed PDFs when using the -e option.pdfid_cmd = /opt/pdftools/pdfid.py#pdfid_opts = -epdfid_opts =[pdf-parser]# Options to run Didier Stevens pdf-parser.py script# pdf_cmd = Path to pdf-parser.py.pdf_cmd = /opt/pdftools/pdf-parser.py[PDF Metadata]# Options for PDF Metadata script# exiftool = path to exitfoolexiftool = /opt/exiftool/exiftool[yara]# Options for the Yara signature plug-in# yara_sigs = Base path to Yara signatures. This path will be recursed# to find additional signatures.# Leave blank to disable the plug-in.yara_sigs = /opt/yara[Digital Signatures]# Options to extract the digital signatures## disitool - path to disitool.py script.# openssl - path to openssl binarydisitool = /opt/disitool/disitool.pyopenssl = /usr/bin/openssl[Office Metadata]# Options for Office Metadata script# exiftool = path to exitfoolexiftool = /opt/exiftool/exiftool[Single-Byte Strings]# options for single-byte string extraction plug-in# length - Minimum length to extractlength = 3# raw - print raw characters instead of formatted ones (e.g. \\n vs. \n)raw = False[ZipExtract]# options for Zip archive file extraction plug-in# enabled: [on|off] - Extract files or not# password: Password to use for zip file. OK to leave blank.enabled = onpassword = infected[Office pyOLEScanner]# olecmd = Path to pyOLEScanner.pyolecmd=/opt/pyOLEScanner/pyOLEScanner.pyEOF
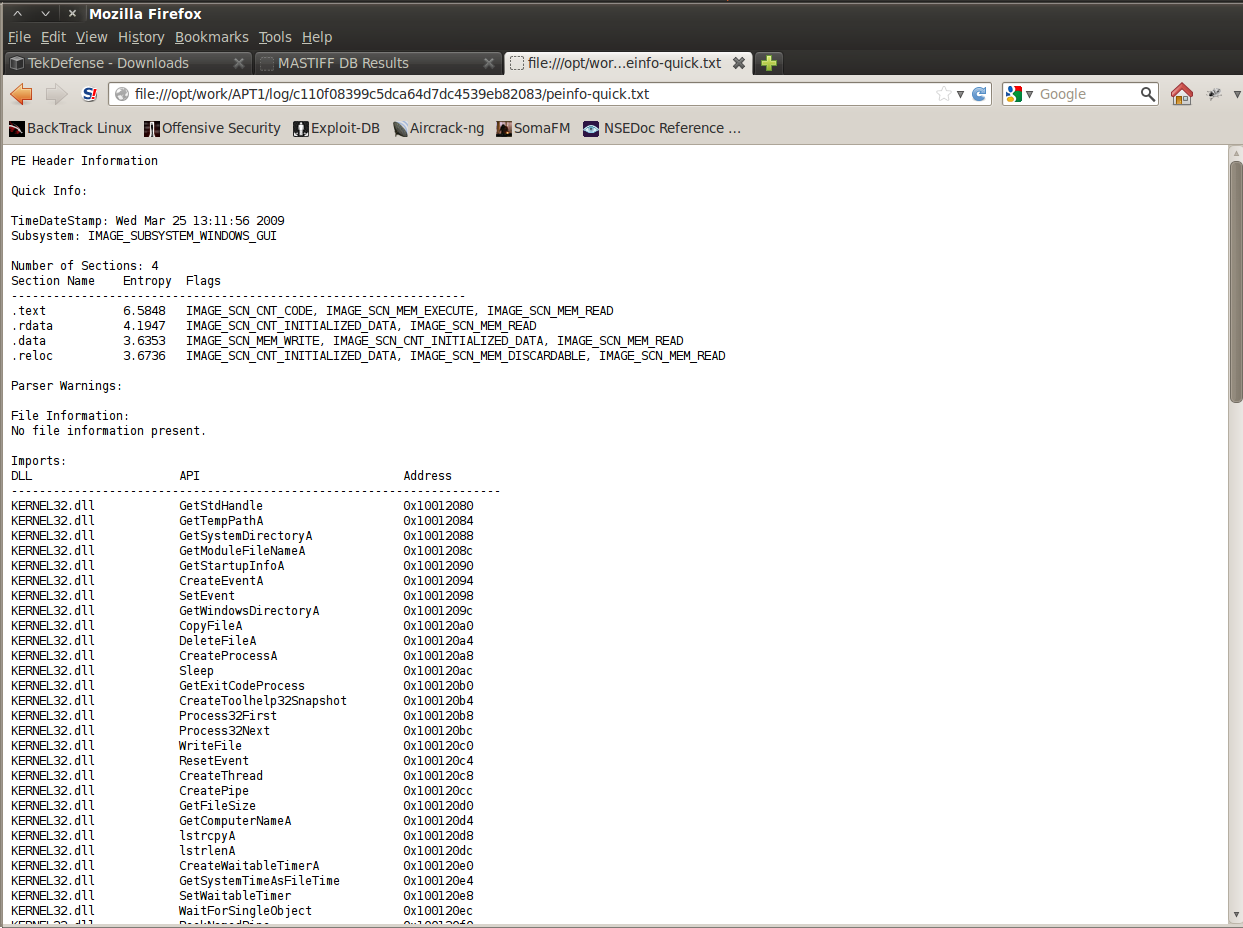
cd /opt/mastiffzwned@malwr:/opt/mastiff$ python mas.py /opt/mastiff/tests/test.exe[2013-03-10 15:11:47,324] [INFO] [Mastiff] : Starting analysis on /opt/mastiff/tests/test.exe[2013-03-10 15:11:47,326] [INFO] [Mastiff.Init_File] : Analyzing /opt/mastiff/tests/test.exe.[2013-03-10 15:11:47,326] [INFO] [Mastiff.Init_File] : Log Directory: ./work/log/c69ffb3057b2077fcaecc99b9f16c7c8[2013-03-10 15:11:47,417] [INFO] [Mastiff.DB.Insert] : Adding ['Generic', 'EXE'][2013-03-10 15:11:47,506] [INFO] [Mastiff.Analysis] : File categories are ['Generic', 'EXE'].[2013-03-10 15:11:47,507] [INFO] [Mastiff.Plugins.Embedded Strings Plugin] : Starting execution.[2013-03-10 15:11:47,521] [INFO] [Mastiff.Plugins.File Information] : Starting execution.[2013-03-10 15:11:47,602] [INFO] [Mastiff.Plugins.Fuzzy Hashing] : Starting execution.[2013-03-10 15:11:47,602] [INFO] [Mastiff.Plugins.Fuzzy Hashing] : Generating fuzzy hash.[2013-03-10 15:11:47,681] [INFO] [Mastiff.Plugins.Fuzzy Hashing.compare] : Comparing fuzzy hashes.[2013-03-10 15:11:47,681] [INFO] [Mastiff.Plugins.VirusTotal] : Starting execution.[2013-03-10 15:11:48,717] [INFO] [Mastiff.Plugins.VirusTotal.submit] : Submission disabled. Not sending file.[2013-03-10 15:11:48,717] [INFO] [Mastiff.Plugins.yara] : Starting execution.[2013-03-10 15:11:48,722] [INFO] [Mastiff.Plugins.Resources] : Starting execution.[2013-03-10 15:11:48,774] [INFO] [Mastiff.Plugins.Single-Byte Strings] : Starting execution.[2013-03-10 15:11:48,813] [INFO] [Mastiff.Plugins.PE Info] : Starting execution.[2013-03-10 15:11:48,926] [INFO] [Mastiff.Plugins.Digital Signatures] : Starting execution.[2013-03-10 15:11:48,975] [INFO] [Mastiff.Plugins.Digital Signatures] : No signature on the file.[2013-03-10 15:11:48,976] [INFO] [Mastiff.Analysis] : Finished analysis for /opt/mastiff/tests/test.exe.zwned@malwr:/opt/mastiff$ python mas.py /opt/mastiff/tests/test.pdf[2013-03-10 15:12:36,299] [INFO] [Mastiff] : Starting analysis on /opt/mastiff/tests/test.pdf[2013-03-10 15:12:36,299] [INFO] [Mastiff.Init_File] : Analyzing /opt/mastiff/tests/test.pdf.[2013-03-10 15:12:36,300] [INFO] [Mastiff.Init_File] : Log Directory: ./work/log/3f53a4bf0097f9075ff641b03bb176f5[2013-03-10 15:12:36,381] [INFO] [Mastiff.DB.Insert] : Adding ['PDF', 'Generic'][2013-03-10 15:12:36,468] [INFO] [Mastiff.Analysis] : File categories are ['PDF', 'Generic'].[2013-03-10 15:12:36,469] [INFO] [Mastiff.Plugins.pdf-parser] : Starting execution.[2013-03-10 15:12:36,470] [INFO] [Mastiff.Plugins.pdf-parser.uncompress] : Uncompressing PDF.[2013-03-10 15:12:36,563] [INFO] [Mastiff.Plugins.pdf-parser.get_objects] : Extracting interesting objects.[2013-03-10 15:12:37,532] [INFO] [Mastiff.Plugins.PDF Metadata] : Starting execution.[2013-03-10 15:12:37,643] [INFO] [Mastiff.Plugins.pdfid] : Starting execution.[2013-03-10 15:12:37,729] [INFO] [Mastiff.Plugins.Embedded Strings Plugin] : Starting execution.[2013-03-10 15:12:37,741] [INFO] [Mastiff.Plugins.File Information] : Starting execution.[2013-03-10 15:12:37,819] [INFO] [Mastiff.Plugins.Fuzzy Hashing] : Starting execution.[2013-03-10 15:12:37,820] [INFO] [Mastiff.Plugins.Fuzzy Hashing] : Generating fuzzy hash.[2013-03-10 15:12:37,909] [INFO] [Mastiff.Plugins.Fuzzy Hashing.compare] : Comparing fuzzy hashes.[2013-03-10 15:12:37,910] [INFO] [Mastiff.Plugins.VirusTotal] : Starting execution.[2013-03-10 15:12:38,386] [INFO] [Mastiff.Plugins.VirusTotal.submit] : Submission disabled. Not sending file.[2013-03-10 15:12:38,386] [INFO] [Mastiff.Plugins.yara] : Starting execution.[2013-03-10 15:12:38,392] [INFO] [Mastiff.Analysis] : Finished analysis for /opt/mastiff/tests/test.pdf.zwned@malwr:/opt/mastiff$ python mas.py /opt/mastiff/tests/test.doc[2013-03-10 15:12:53,882] [INFO] [Mastiff] : Starting analysis on /opt/mastiff/tests/test.doc[2013-03-10 15:12:53,883] [INFO] [Mastiff.Init_File] : Analyzing /opt/mastiff/tests/test.doc.[2013-03-10 15:12:53,883] [INFO] [Mastiff.Init_File] : Log Directory: ./work/log/759f7e53f54df03f2ae06fcec25e8ac3[2013-03-10 15:12:53,973] [INFO] [Mastiff.DB.Insert] : Adding ['Generic', 'Office', 'ZIP'][2013-03-10 15:12:54,076] [INFO] [Mastiff.Analysis] : File categories are ['Generic', 'Office', 'ZIP'].[2013-03-10 15:12:54,078] [INFO] [Mastiff.Plugins.Embedded Strings Plugin] : Starting execution.[2013-03-10 15:12:54,088] [INFO] [Mastiff.Plugins.File Information] : Starting execution.[2013-03-10 15:12:54,167] [INFO] [Mastiff.Plugins.Fuzzy Hashing] : Starting execution.[2013-03-10 15:12:54,167] [INFO] [Mastiff.Plugins.Fuzzy Hashing] : Generating fuzzy hash.[2013-03-10 15:12:54,234] [INFO] [Mastiff.Plugins.Fuzzy Hashing.compare] : Comparing fuzzy hashes.[2013-03-10 15:12:54,234] [INFO] [Mastiff.Plugins.VirusTotal] : Starting execution.[2013-03-10 15:12:55,239] [INFO] [Mastiff.Plugins.yara] : Starting execution.[2013-03-10 15:12:55,244] [INFO] [Mastiff.Plugins.Office pyOLEScanner] : Starting execution.[2013-03-10 15:12:57,497] [INFO] [Mastiff.Plugins.Office Metadata] : Starting execution.[2013-03-10 15:12:57,681] [INFO] [Mastiff.Plugins.ZipInfo] : Starting execution.[2013-03-10 15:12:57,682] [INFO] [Mastiff.Plugins.ZipExtract] : Starting execution.[2013-03-10 15:12:57,683] [INFO] [Mastiff.Plugins.ZipExtract] : Password "infected" will be used for this zip.[2013-03-10 15:12:57,683] [INFO] [Mastiff.Plugins.ZipExtract] : Extracting [Content_Types].xml.[2013-03-10 15:12:57,683] [INFO] [Mastiff.Plugins.ZipExtract] : Extracting _rels/.rels.[2013-03-10 15:12:57,684] [INFO] [Mastiff.Plugins.ZipExtract] : Extracting theme/theme/themeManager.xml.[2013-03-10 15:12:57,684] [INFO] [Mastiff.Plugins.ZipExtract] : Extracting theme/theme/theme1.xml.[2013-03-10 15:12:57,685] [INFO] [Mastiff.Plugins.ZipExtract] : Extracting theme/theme/_rels/themeManager.xml.rels.[2013-03-10 15:12:57,685] [INFO] [Mastiff.Analysis] : Finished analysis for /opt/mastiff/tests/test.doc.zwned@malwr:/opt/mastiff$ python mas.py /opt/mastiff/tests/test.test.doc test.exe test.pdf test.zipzwned@malwr:/opt/mastiff$ python mas.py /opt/mastiff/tests/test.zip[2013-03-10 15:13:22,856] [INFO] [Mastiff] : Starting analysis on /opt/mastiff/tests/test.zip[2013-03-10 15:13:22,870] [INFO] [Mastiff.Init_File] : Analyzing /opt/mastiff/tests/test.zip.[2013-03-10 15:13:22,871] [INFO] [Mastiff.Init_File] : Log Directory: ./work/log/033d488bbe65e8aececb2c55bdfbc2fd[2013-03-10 15:13:23,035] [INFO] [Mastiff.DB.Insert] : Adding ['Generic', 'ZIP'][2013-03-10 15:13:23,106] [INFO] [Mastiff.Analysis] : File categories are ['Generic', 'ZIP'].[2013-03-10 15:13:23,107] [INFO] [Mastiff.Plugins.Embedded Strings Plugin] : Starting execution.[2013-03-10 15:13:23,115] [INFO] [Mastiff.Plugins.File Information] : Starting execution.[2013-03-10 15:13:23,178] [INFO] [Mastiff.Plugins.Fuzzy Hashing] : Starting execution.[2013-03-10 15:13:23,178] [INFO] [Mastiff.Plugins.Fuzzy Hashing] : Generating fuzzy hash.[2013-03-10 15:13:23,238] [INFO] [Mastiff.Plugins.Fuzzy Hashing.compare] : Comparing fuzzy hashes.[2013-03-10 15:13:23,238] [INFO] [Mastiff.Plugins.VirusTotal] : Starting execution.[2013-03-10 15:13:23,440] [INFO] [Mastiff.Plugins.VirusTotal.submit] : Submission disabled. Not sending file.[2013-03-10 15:13:23,440] [INFO] [Mastiff.Plugins.yara] : Starting execution.[2013-03-10 15:13:23,445] [INFO] [Mastiff.Plugins.ZipInfo] : Starting execution.[2013-03-10 15:13:23,446] [INFO] [Mastiff.Plugins.ZipExtract] : Starting execution.[2013-03-10 15:13:23,447] [INFO] [Mastiff.Plugins.ZipExtract] : Password "infected" will be used for this zip.[2013-03-10 15:13:23,447] [INFO] [Mastiff.Plugins.ZipExtract] : Extracting test.bin.[2013-03-10 15:13:23,447] [INFO] [Mastiff.Plugins.ZipExtract] : Extracting test.txt.[2013-03-10 15:13:23,448] [INFO] [Mastiff.Analysis] : Finished analysis for /opt/mastiff/tests/test.zip.
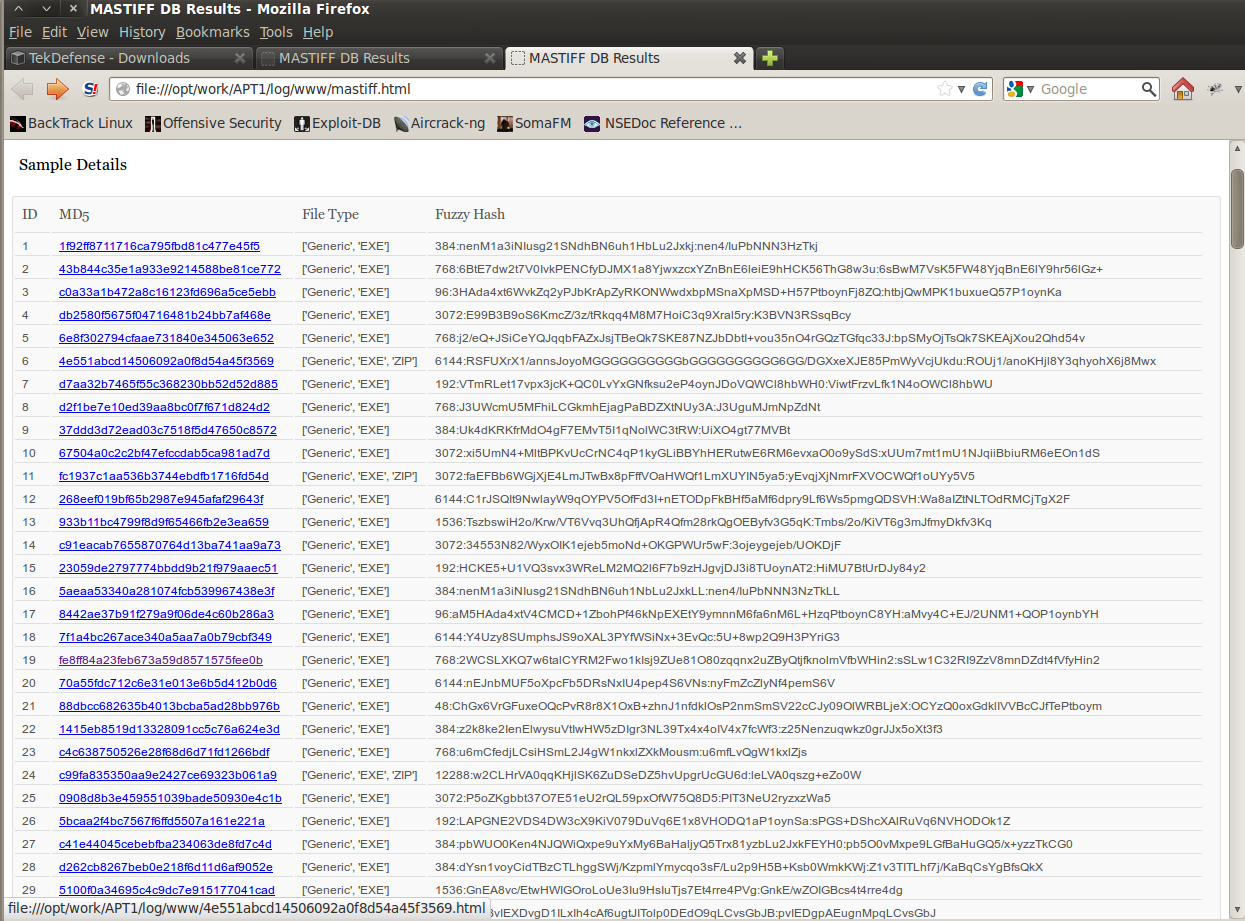
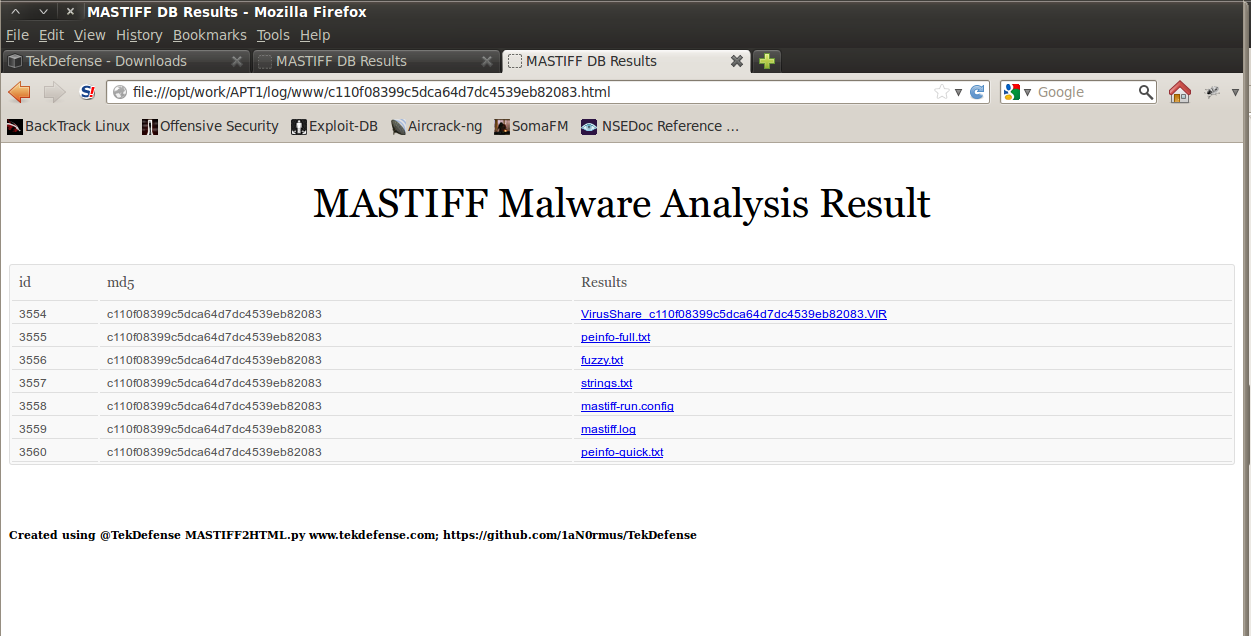
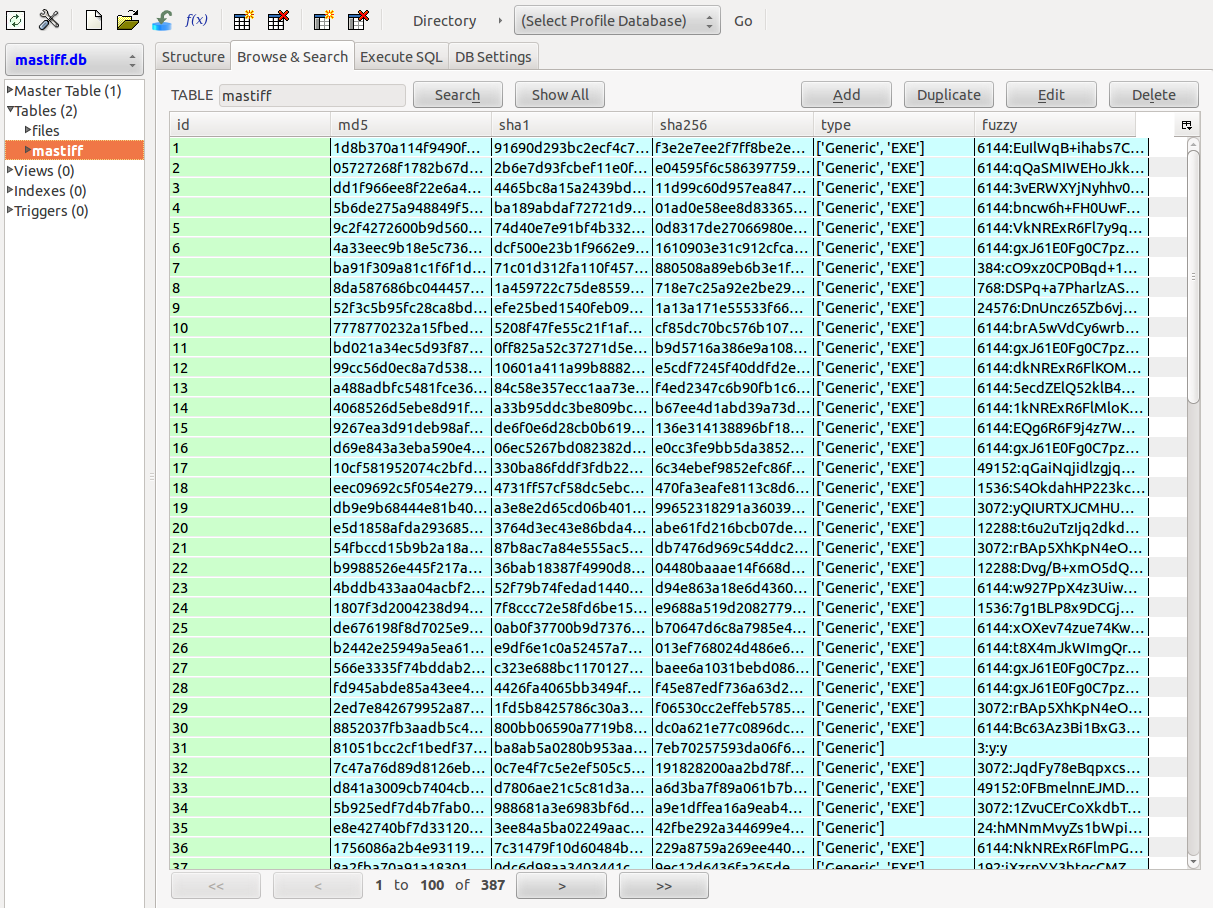
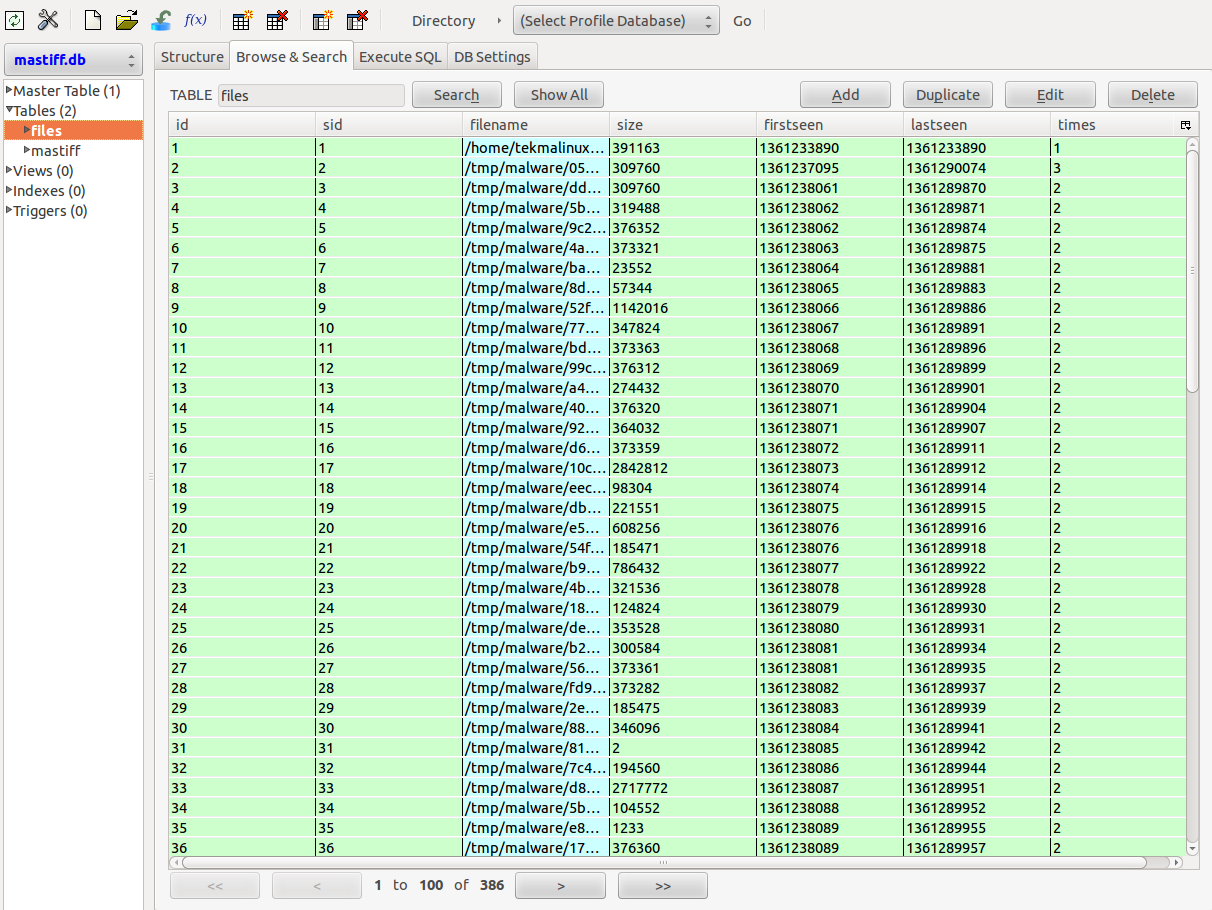
wget https://raw.github.com/1aN0rmus/TekDefense/master/MASTIFF2HTML.pychmod +x MASTIFF2HTML.pypython MASTIFF2HTML.py -f /opt/mastiff/work/log/ -d mastiff.dbcd /opt/mastiff/work/log/www/python -m SimpleHTTPServer
 Install,
Install,  MASTIFF,
MASTIFF,  Malware,
Malware,  Malware analysis in
Malware analysis in  News
News