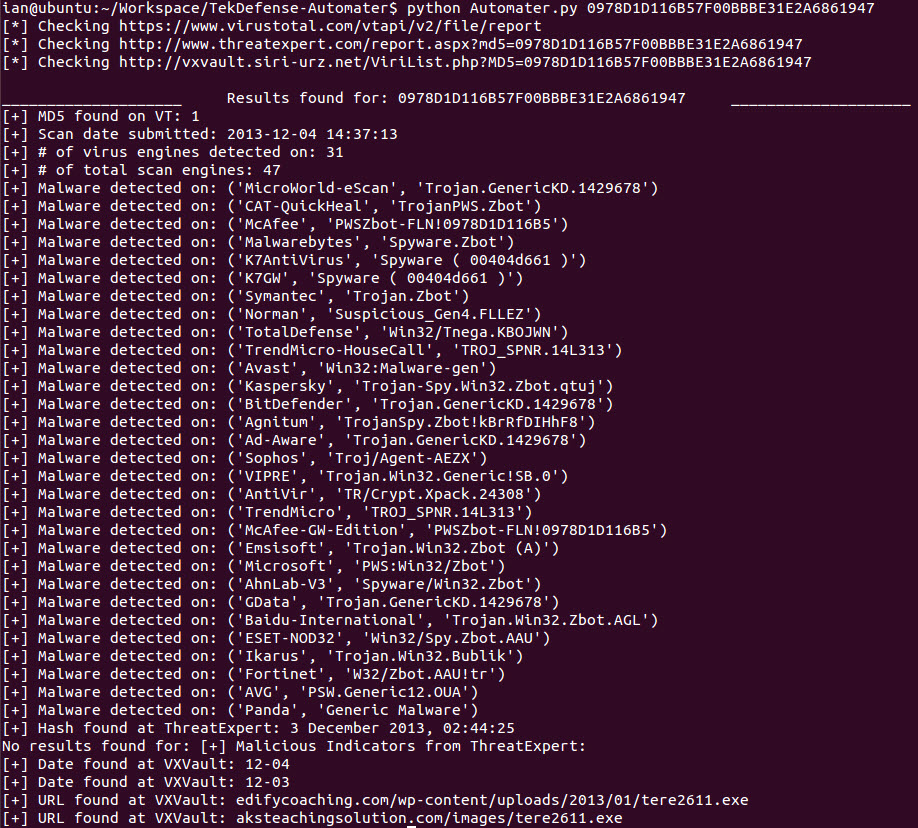
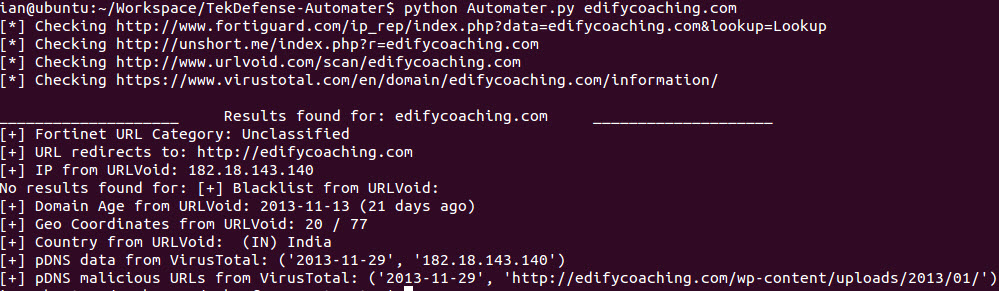
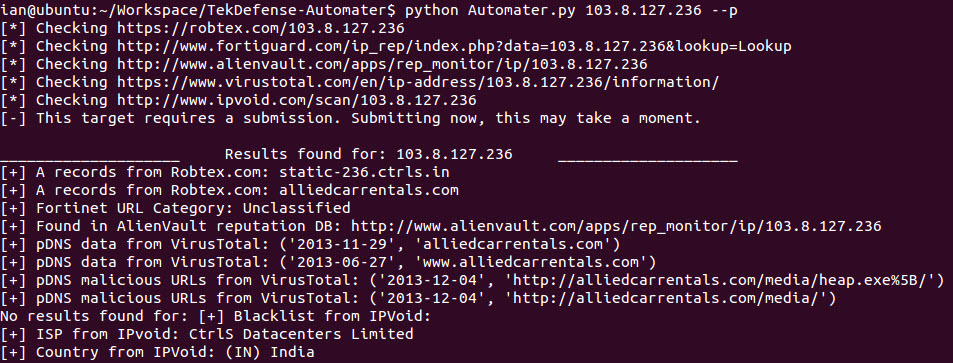
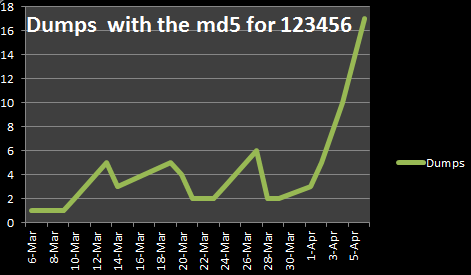
root@bt:~/workspace/Automater# ./hashCollect.py -u http://pastebin.com/2ysAGFJY
6b586e2d4ca26d9438589a85585ca0b2
db17a0bf8505f7620291a8efc466ce86
5a815fd388b6027b949d58977277a006
dbab8786ed0eca3dbb82e401ce976d7e
d772ffda95ce3417456c80a8f85606d2
a9e9f1c9d9296f0c38467efc7dca1a24
96f003089b0ad3a71261ed5a1533c794
39dcaf7a053dc372fbc391d4e6b5d693
5079a6b1fb2015dbdb0c4b205f917307
1349437e3137826639b4f5165bc7e02b
3f94e8774be14358a45e2dda6a60216a
ce5225d01c39d2567bc229501d9e610d
6403675579f6114559c90de0014cd3d6
81dc9bdb52d04dc20036dbd8313ed055
81dc9bdb52d04dc20036dbd8313ed055
c67fc3a08cc21eaecb0fadf68129c314
4e270f490ab6943cbfbe95c9b936d7bb
81dc9bdb52d04dc20036dbd8313ed055
348a6a2356c3aebe392aaad3f646c30c
0e69229f5978ebc338f2cfb8cc8caad1
dc1caba8d678508cc3f6985ae35d7c9f
4f4bdca0d270dbbff6647a356fe2ba3f
e41a2cb50c3362f0015404effec8761e
1e4a9c23007eb10f758cbf3362c8ae41
b59c67bf196a4758191e42f76670ceba
15de21c670ae7c3f6f3f1f37029303c9
44d61d552280cf5e9c55dc11ff18cbf2
1794e1d48bbf9f73d53dec1951f053d2
bb2782795456847fb533d51eefd9d360
fe43196710222556c8bcc1c23c022a74
81dc9bdb52d04dc20036dbd8313ed055
0a03d5e4473c0629cfb20c5c31543b06
fe43196710222556c8bcc1c23c022a74
c944634550c698febdd9c868db908d9d
c944634550c698febdd9c868db908d9d
c944634550c698febdd9c868db908d9d
9e94b15ed312fa42232fd87a55db0d39
a01610228fe998f515a72dd730294d87
c0079e0d4e801bc94bce6fa2ed9e008c
ece5cdf7b946687f0077abb714054a65
a31e7b7f49ae4bb4dcc460d51b0bada0
e13b330c974ba77aef5bd4504eebe5e9
cd474f6341aeffd65f93084d0dae3453
4eceed354639b6ed2b236be2eb5a065e
7e7e69ea3384874304911625ac34321c
c889144fa7ab1a735872c290d8781899
2fbec6c8aa22b895bc40efa6e89b4bac
8621c6b58f7dde244ad2261610383fae
05a70454516ecd9194c293b0e415777f
192cc6356b292ce2a105c222ab6042ae
784ec60b05fc2eaa5c74e4775220fbb1
fdcfc3f14ebf698bbd76b1157ef709fa
e10adc3949ba59abbe56e057f20f883e
e0c64dbc8cb6abc98a0c696d168ebdb9
82ce647f22861f30627ee0ae50ce0adb
02cc9f0bf98299b63cdfd77fbfec7172
44dc880ec5f9237fa80be3177161fc6f
fdcfc3f14ebf698bbd76b1157ef709fa
fe01ce2a7fbac8fafaed7c982a04e229
29988429c481f219b8c5ba8c071440e1
42bb5b74add1fe6bb353cf5e14562fb6
41ad29597e715721522a30733b96a6f3
2a85ca2b0c07c342facc02ac61d57171
4ffc938c6c948859ce9c4ec827e1e40a
6967cabefd763ac1a1a88e11159957db
33026ce64a49d23be2d07d04b6ef4384
f9a13a115a69b22323e7ef9ef9fedcb6
f92e053a1fd2c673cb899db192ad0f2e
8cbfe3eb54787170a9ad6af435964828
d860b866e9023673fd802d97b97fc357
e391997bd526a092ac4d7f9b50da8904
ae0e4bdad7b5f67141743366026d2ea5
e10adc3949ba59abbe56e057f20f883e
c4de8ced6214345614d33fb0b16a8acd
4ddc0354b46b390a933bb6d2353fff26
fa1ee3a6f55b9b5cacc571a76c3842a1
de38aee67bacae29c2e8d868418293bd
a381c2c35c9157f6b67fd07d5a200ae1
5bc06f5800d415cc95e1349edbaca425
902fbdd2b1df0c4f70b4a5d23525e932
aa15b9243a9f99d122d5803606e3c4df
e10adc3949ba59abbe56e057f20f883e
3514603c3f975120a33354aeed9039a3
da897ba0fe30eff270424ac0e768840f
2be5b6590b60d5f4eca7e13c4083af7e
f502e183d729ab3ad224f1dfcc0708e2
c5fe25896e49ddfe996db7508cf00534
c9dab21c609875c00eaa19f04d19e2d0
b0253ef863f3a4a2e746c793fa71ae7d
46f0cac183682913b2d9e685cd7da3a7
4ef02ee44e55ca014df93b75eb956103
1618a9fe1c58f2bedd2fdccefaa6da21
1618a9fe1c58f2bedd2fdccefaa6da21
abc2e2f32e486fc2e1072003cc88149a
b269e1a566f861efa042e7ea7a08b062
8562ae5e286544710b2e7ebe9858833b
4251dd1cece37b7ee6ba2c2e40039bdd
204f8213a4cc1aaffa1fb123406d1ae9
8bb75b3015682d910daf88b6d728be2c
ff2cd3d917770fdcbbd541faf5423413
c91793b6ef51da231364176994d678a9
b76c3936d26110aad104844a0496e614
827ccb0eea8a706c4c34a16891f84e7b
4297f44b13955235245b2497399d7a93
775df0ec6881d9fcb545b5cd5a409873
ae950f6eecfe4d911b6b959ec3965231
d726335216d643e3c467eb0cdfc3d4e7
1dfa9fe971cd0711ce70e794063bea22
1311c5a589710f5030ae0fa36a20774c
e85984bd537ecc6d027b43bef22e4f12
dab456a52cb642e187cd307a5cfbef79
81dc9bdb52d04dc20036dbd8313ed055
 Wednesday, December 4, 2013 at 10:04AM
Wednesday, December 4, 2013 at 10:04AM