Tektip ep27 - hashCollect.py
 Sunday, April 7, 2013 at 4:34PM
Sunday, April 7, 2013 at 4:34PM With the #OpIsreal stuff going on right now there has been many more password dumps put out than usual. For instance using Andrew Mohawks PasteLert web app I get alerted anytime there is a pastebin post that includes the hash e10adc3949ba59abbe56e057f20f883e. e10adc3949ba59abbe56e057f20f883e is the hash of the most common password: 123456. I set up the alert for this hash because it will catch password dumps regardless of the language. I admit there are some faults though, particularly if the site that the passwords are dumped from have password requirements that would not allow a password of 123456. The following is a graph that shows the typical number of dumps I see with these parameters:
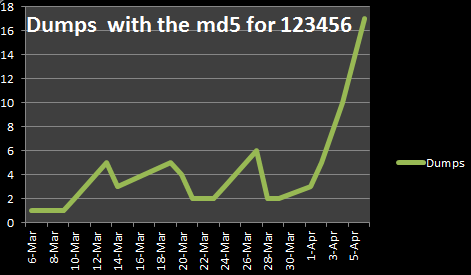
As you can see, #OpIsreal has caused a significant uptick in the number of password dumps that include the hash for 123456.
My typical process once I get a hold of the dumps from these is I download the file, manually pull out the typical header data like the name of the operation and all the propaganda, then I use the cut command to pull out just the hashes. While this isn't too lengthy of a process, I am a lazy man. From this laziness, comes hashCollect.py.
HashCollect.py is a python tool I wrote that will scrape md5 hashes out of a specific file or url. While this script is pretty bare right now it gets the job done. I have many plans for it, that you will hopefully see soon.
You can dowload hashCollect along with my other scripts at GitHub.
The help command will show the options:
root@bt:~/workspace/Automater# ./hashCollect.py -husage: hashCollect.py [-h] [-u URL] [-f FILE] [-o OUTPUT]Hash Collectoroptional arguments:-h, --help show this help message and exit-u URL, --url URL This option is used to search for hashes on a website-f FILE, --file FILE This option is used to import a file that containshashes-o OUTPUT, --output OUTPUTThis option will output the results to a file.
root@bt:~/workspace/Automater# ./hashCollect.py -f hashes09a85c0ef4169a24210d741838e8c8d943a9b1c680ea8f8df293e58b9ce77b9d9f22025be8346e4d4d7db80ed890b511f1887d3f9e6ee7a32fe5e76f4ab80d63704992a0216ae39f1ebf3771fd5cd23ca5915fe9b6ed8d251fd342b74106e34b16ea0d4fadc502c247209194645e4f4a9719536c0f2d1a578b323853998e03ba93279e3308bdbbeed946fc965017f67ade46896de0010ae616f9c6cb3f7e4cfcbd9b23306ab802765a63870b29d1239bb3d6288bfd707aee52db620839f3a38125d55ad283aa400af464c76d713c07ad17e6ec4b774be1bfbd12e26a68f9d9bf7d8c3a265ad7aa2f4e20b1a93fde3c541c2f7107394f0d29999a1c23e1deaf4453c86172178bc31dacba8b501f34b976aa2b0de3de9b517b592059ca5d6cfa4ccaac935aae3e50060442ee55bc9e1a3f9824bbc389f1c39f2b2cdfa839938d05a474b36564cc2730d27f716f3c7c2fe1236558a7ec33e3223db4471024833013f229ea34d627074a1fd0a474f4a51c7be10adc3949ba59abbe56e057f20f883ea474b36564cc2730d27f716f3c7c2fe1fd5972161600fb43f057efd443d77589aa881d0c78e0e60642e006ca88c9495fe10adc3949ba59abbe56e057f20f883e1a92fc27d687aefa619c24851cbb121349518adbec43b4264c0ea840c2e233d51f247e3f69c363f18dec2e343008d142
root@bt:~/workspace/Automater# ./hashCollect.py -u http://pastebin.com/2ysAGFJY6b586e2d4ca26d9438589a85585ca0b2db17a0bf8505f7620291a8efc466ce865a815fd388b6027b949d58977277a006dbab8786ed0eca3dbb82e401ce976d7ed772ffda95ce3417456c80a8f85606d2a9e9f1c9d9296f0c38467efc7dca1a2496f003089b0ad3a71261ed5a1533c79439dcaf7a053dc372fbc391d4e6b5d6935079a6b1fb2015dbdb0c4b205f9173071349437e3137826639b4f5165bc7e02b3f94e8774be14358a45e2dda6a60216ace5225d01c39d2567bc229501d9e610d6403675579f6114559c90de0014cd3d681dc9bdb52d04dc20036dbd8313ed05581dc9bdb52d04dc20036dbd8313ed055c67fc3a08cc21eaecb0fadf68129c3144e270f490ab6943cbfbe95c9b936d7bb81dc9bdb52d04dc20036dbd8313ed055348a6a2356c3aebe392aaad3f646c30c0e69229f5978ebc338f2cfb8cc8caad1dc1caba8d678508cc3f6985ae35d7c9f4f4bdca0d270dbbff6647a356fe2ba3fe41a2cb50c3362f0015404effec8761e1e4a9c23007eb10f758cbf3362c8ae41b59c67bf196a4758191e42f76670ceba15de21c670ae7c3f6f3f1f37029303c944d61d552280cf5e9c55dc11ff18cbf21794e1d48bbf9f73d53dec1951f053d2bb2782795456847fb533d51eefd9d360fe43196710222556c8bcc1c23c022a7481dc9bdb52d04dc20036dbd8313ed0550a03d5e4473c0629cfb20c5c31543b06fe43196710222556c8bcc1c23c022a74c944634550c698febdd9c868db908d9dc944634550c698febdd9c868db908d9dc944634550c698febdd9c868db908d9d9e94b15ed312fa42232fd87a55db0d39a01610228fe998f515a72dd730294d87c0079e0d4e801bc94bce6fa2ed9e008cece5cdf7b946687f0077abb714054a65a31e7b7f49ae4bb4dcc460d51b0bada0e13b330c974ba77aef5bd4504eebe5e9cd474f6341aeffd65f93084d0dae34534eceed354639b6ed2b236be2eb5a065e7e7e69ea3384874304911625ac34321cc889144fa7ab1a735872c290d87818992fbec6c8aa22b895bc40efa6e89b4bac8621c6b58f7dde244ad2261610383fae05a70454516ecd9194c293b0e415777f192cc6356b292ce2a105c222ab6042ae784ec60b05fc2eaa5c74e4775220fbb1fdcfc3f14ebf698bbd76b1157ef709fae10adc3949ba59abbe56e057f20f883ee0c64dbc8cb6abc98a0c696d168ebdb982ce647f22861f30627ee0ae50ce0adb02cc9f0bf98299b63cdfd77fbfec717244dc880ec5f9237fa80be3177161fc6ffdcfc3f14ebf698bbd76b1157ef709fafe01ce2a7fbac8fafaed7c982a04e22929988429c481f219b8c5ba8c071440e142bb5b74add1fe6bb353cf5e14562fb641ad29597e715721522a30733b96a6f32a85ca2b0c07c342facc02ac61d571714ffc938c6c948859ce9c4ec827e1e40a6967cabefd763ac1a1a88e11159957db33026ce64a49d23be2d07d04b6ef4384f9a13a115a69b22323e7ef9ef9fedcb6f92e053a1fd2c673cb899db192ad0f2e8cbfe3eb54787170a9ad6af435964828d860b866e9023673fd802d97b97fc357e391997bd526a092ac4d7f9b50da8904ae0e4bdad7b5f67141743366026d2ea5e10adc3949ba59abbe56e057f20f883ec4de8ced6214345614d33fb0b16a8acd4ddc0354b46b390a933bb6d2353fff26fa1ee3a6f55b9b5cacc571a76c3842a1de38aee67bacae29c2e8d868418293bda381c2c35c9157f6b67fd07d5a200ae15bc06f5800d415cc95e1349edbaca425902fbdd2b1df0c4f70b4a5d23525e932aa15b9243a9f99d122d5803606e3c4dfe10adc3949ba59abbe56e057f20f883e3514603c3f975120a33354aeed9039a3da897ba0fe30eff270424ac0e768840f2be5b6590b60d5f4eca7e13c4083af7ef502e183d729ab3ad224f1dfcc0708e2c5fe25896e49ddfe996db7508cf00534c9dab21c609875c00eaa19f04d19e2d0b0253ef863f3a4a2e746c793fa71ae7d46f0cac183682913b2d9e685cd7da3a74ef02ee44e55ca014df93b75eb9561031618a9fe1c58f2bedd2fdccefaa6da211618a9fe1c58f2bedd2fdccefaa6da21abc2e2f32e486fc2e1072003cc88149ab269e1a566f861efa042e7ea7a08b0628562ae5e286544710b2e7ebe9858833b4251dd1cece37b7ee6ba2c2e40039bdd204f8213a4cc1aaffa1fb123406d1ae98bb75b3015682d910daf88b6d728be2cff2cd3d917770fdcbbd541faf5423413c91793b6ef51da231364176994d678a9b76c3936d26110aad104844a0496e614827ccb0eea8a706c4c34a16891f84e7b4297f44b13955235245b2497399d7a93775df0ec6881d9fcb545b5cd5a409873ae950f6eecfe4d911b6b959ec3965231d726335216d643e3c467eb0cdfc3d4e71dfa9fe971cd0711ce70e794063bea221311c5a589710f5030ae0fa36a20774ce85984bd537ecc6d027b43bef22e4f12dab456a52cb642e187cd307a5cfbef7981dc9bdb52d04dc20036dbd8313ed055
root@bt:~/workspace/Automater# ./hashCollect.py -u http://pastebin.com/2ysAGFJY -o /tmp/outputfileforhashes.txt
[+] Printing results to file: /tmp/outputfileforhashes.txt
That's it for now, but I will grow this out soon. Some of the features I am thinking about adding are:
- Allow custom regex
- Allow for pulling other hashes like SHA256
- Check hashes against online hash crackers
- Output to a database
- Create a frontend
- What would you like to see?
Have any suggestions. Let me know 1aN0rmus@TekDefense.com.
 Admin |
Admin |  Post a Comment |
Post a Comment |