Tektip ep25 - Static Malware Analysis With PEFRAME
 Sunday, March 17, 2013 at 11:49AM
Sunday, March 17, 2013 at 11:49AM In this episode of TekTip we cover using peframe to help with the automating of static analysis of Portable Executable (PE) files. While MASTIFF (which we covered extensively) will determine a file type and then based on the file type run the appropriate tools, peframe focuses specifically on PE files or what we generally consider standard windows executables. This focus allows peframe to pull out some great data that we don't see (at least not yet), in other static analysis frameworks.
Peframe was created by Gianni Amato (@guelfoweb) and added to the CAINE digital forensics distro.
Like MASTIFF peframe at its current release can only run against a single file at a time. The script I wrote to automate running MASTIFF against multiple files could be easily modified to do the same for peframe.
Installation for peframe is simple, just download the zip and extract to the directory you want to run it from, for me I chose /opt/peframe. The only dependencies I am aware of are python 2.7, and peid.
OPTIONS:-h --help This help-a --auto Show Auto analysis-i --info PE file attributes--hash Hash MD5 & SHA1--meta Version info & metadata--peid PE Identifier Signature--antivm Anti Virtual Machine--antidbg Anti Debug | Disassembler--sections Section analyzer--functions Imported DLLs & API functions--suspicious Search for suspicious API & sections--dump Dumping all the information--strings Extract all the string--url Extract File Name and Url--hexdump Reverse Hex dump--import List Entry Import instances--export List Entry Export instances--resource List Entry Resource instances--debug List Entry DebugData instances
Example Usage:
For must the auto option will pull all the data needed.
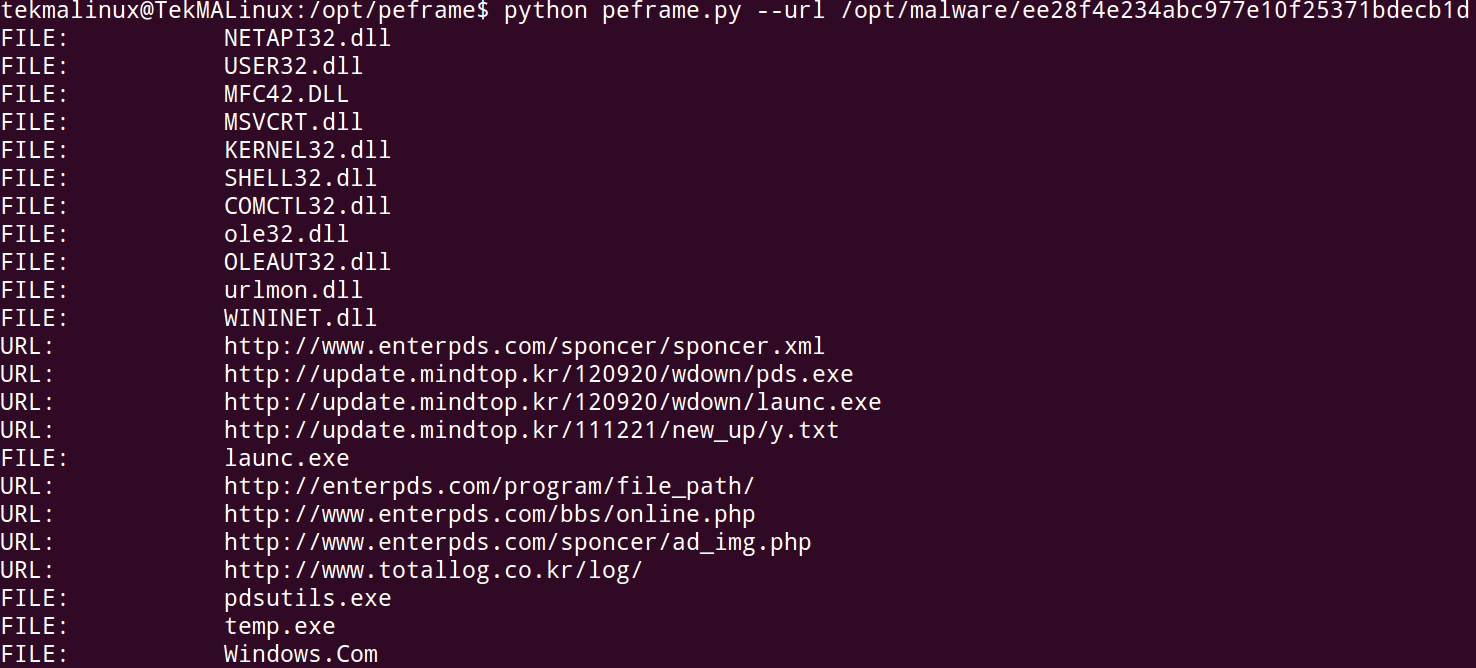
tekmalinux@TekMALinux:/opt/peframe$ sudo python peframe.py --auto /opt/malware/e72f79a5399c84f11d954ce59e4186f2
File Name: e72f79a5399c84f11d954ce59e4186f2
File Size: 752424 byte
Compile Time: 2013-02-26 17:35:54
DLL: False
Sections: 5
MD5 hash: e72f79a5399c84f11d954ce59e4186f2
SHA-1 hash: 8ed3ec95756f7be133f3e94309e0d22795f6da75
Packer: Microsoft Visual C++ 8
Anti Debug: Yes
Anti VM: None
File and URL:
FILE: ntdll.dll
FILE: kernel32.dll
FILE: s.dll
FILE: comctl32.dll
FILE: comdlg32.dll
FILE: shell32.dll
FILE: WININET.DLL
FILE: mfcm90.dll
FILE: user32.dll
FILE: ole32.dll
FILE: .com
FILE: .bat
FILE: .exe
FILE: USER32.DLL
FILE: OLEACC.dll
FILE: gdiplus.dll
FILE: RPCRT4.dll
FILE: VERSION.dll
FILE: KERNEL32.dll
FILE: USER32.dll
FILE: GDI32.dll
FILE: COMDLG32.dll
FILE: ADVAPI32.dll
FILE: SHELL32.dll
FILE: COMCTL32.dll
FILE: SHLWAPI.dll
FILE: oledlg.dll
FILE: ole32.dll
FILE: OLEAUT32.dll
FILE: urlmon.dll
FILE: WININET.dll
URL: http://schemas.microsoft.com/SMI/2005/WindowsSettings
FILE: Windows.Com
URL: http://crl.verisign.com/pca3.crl0
URL: https://www.verisign.com/cps0
URL: http://logo.verisign.com/vslogo.gif04
URL: http://ocsp.verisign.com0
URL: http://logo.verisign.com/vslogo.gif0
URL: https://www.verisign.com/rpa
URL: http://csc3-2010-crl.verisign.com/CSC3-2010.crl0D
URL: https://www.verisign.com/rpa0
URL: http://ocsp.verisign.com0
URL: http://csc3-2010-aia.verisign.com/CSC3-2010.cer0
URL: https://www.verisign.com/rpa
URL: http://csc3-2010-crl.verisign.com/CSC3-2010.crl0D
URL: https://www.verisign.com/rpa0
URL: http://ocsp.verisign.com0
URL: http://csc3-2010-aia.verisign.com/CSC3-2010.cer0
URL: https://www.verisign.com/rpa
URL: https://www.verisign.com/cps0
URL: https://www.verisign.com/rpa0
URL: http://logo.verisign.com/vslogo.gif04
URL: http://crl.verisign.com/pca3-g5.crl04
URL: http://ocsp.verisign.com0
URL: https://www.verisign.com/rpa
Suspicious API Functions:
Func. Name: GetFileAttributesA
Func. Name: GetFileSizeEx
Func. Name: GetModuleHandleW
Func. Name: UnhandledExceptionFilter
Func. Name: IsDebuggerPresent
Func. Name: GetDriveTypeA
Func. Name: GetCommandLineA
Func. Name: GetStartupInfoA
Func. Name: VirtualProtect
Func. Name: VirtualAlloc
Func. Name: ExitThread
Func. Name: CreateThread
Func. Name: FindNextFileA
Func. Name: CreateFileA
Func. Name: FindFirstFileA
Func. Name: GetFileSize
Func. Name: WriteFile
Func. Name: GetModuleFileNameW
Func. Name: GetModuleHandleA
Func. Name: CreateProcessA
Func. Name: GetTempFileNameA
Func. Name: DeleteFileA
Func. Name: CreateDirectoryA
Func. Name: GetTickCount
Func. Name: LoadLibraryA
Func. Name: LoadLibraryA
Func. Name: GetProcAddress
Func. Name: CreateToolhelp32Snapshot
Func. Name: Process32First
Func. Name: Process32Next
Func. Name: OpenProcess
Func. Name: TerminateProcess
Func. Name: GetTempPathA
Func. Name: GetModuleFileNameA
Func. Name: GetVersionExA
Func. Name: Sleep
Func. Name: FindResourceA
Func. Name: LockResource
Func. Name: CreateFileW
Func. Name: GetWindowThreadProcessId
Func. Name: SetWindowsHookExA
Func. Name: RegOpenKeyA
Func. Name: RegCreateKeyExA
Func. Name: RegCloseKey
Func. Name: RegEnumKeyA
Func. Name: RegDeleteKeyA
Func. Name: RegOpenKeyExA
Func. Name: ShellExecuteA
Func. Name: URLDownloadToFileA
Func. Name: InternetConnectA
Func. Name: HttpSendRequestA
Func. Name: InternetReadFile
Func. Name: InternetWriteFile
Func. Name: InternetOpenA
Func. Name: InternetCloseHandle
Func. Name: HttpQueryInfoA
Func. Name: InternetQueryDataAvailable
Func. Name: InternetQueryDataAvailable
Func. Name: InternetCrackUrlA
Suspicious API Anti-Debug:
Anti Debug: UnhandledExceptionFilter
Anti Debug: IsDebuggerPresent
Anti Debug: Process32First
Anti Debug: Process32Next
Anti Debug: TerminateProcess
Anti Debug: GetWindowThreadProcessId
Suspicious Sections:
InternalName: Setup.exe
FileVersion: 2.4.2
CompanyName: DownloadManager
ProductName: DownloadManager.exe
ProductVersion: 2.4.2
FileDescription: DownloadManager
OriginalFilename: Setup.exe
Translation: 0x0409 0x04e4
Now of course, if you don't want all the information that the auto option gives you can run the indivual options themselves. Additionally, you can use the --dump, --strings, --hexdump options to pull out more data if the auto option didn't give you what you want.
Overall, I think peframe is a great tool. While it runs many of the tools that we see in other frameworks it also applies a little analytics to the results pointing out key data like, file names, urls, Anti Forensics techniques, and suspicious API calls.
 Admin |
Admin |  Post a Comment |
Post a Comment |