While most of us probably live in the linux world where their are already built in text editors that allow for much of the functionality I will speak to today, there are many that use Windows as their primary box. In some cases our employers push Windows on us, as they don't trust open source.
Either way we all probably have a windows box somewhere, even if it is just for malware analysis, or dare I say gaming. Notepad++ is THE text editor to use in these situations. With a large community building plugins, the features are limitless. Today though we will be focusing on the Regex capabilities.
2013-01-06 05:35:50+0000 [SSHService ssh-userauth on HoneyPotTransport,516,210.14.71.201] login attempt [root/masinadescule] failed
2013-01-06 05:35:54+0000 [SSHService ssh-userauth on HoneyPotTransport,517,210.14.71.201] login attempt [admin/.sfl@zk^] failed
2013-01-06 05:35:58+0000 [SSHService ssh-userauth on HoneyPotTransport,518,210.14.71.201] login attempt [root/zaq123] failed
2013-01-06 05:36:02+0000 [SSHService ssh-userauth on HoneyPotTransport,519,210.14.71.201] login attempt [root/==============down=================] failed
2013-01-06 05:36:06+0000 [SSHService ssh-userauth on HoneyPotTransport,520,210.14.71.201] login attempt [bin/!!(@(*#*))MNNNBHSA{{":**(@] failed
2013-01-06 05:36:11+0000 [SSHService ssh-userauth on HoneyPotTransport,521,210.14.71.201] login attempt [bin/2#%#@%$] failed
2013-01-06 05:36:14+0000 [SSHService ssh-userauth on HoneyPotTransport,522,210.14.71.201] login attempt [bin/510326mazda] failed
2013-01-06 05:36:18+0000 [SSHService ssh-userauth on HoneyPotTransport,523,210.14.71.201] login attempt [bin/FSDwef8529637531598273k1d123kid871kid872tralalalovedolce] failed
2013-01-06 05:36:22+0000 [SSHService ssh-userauth on HoneyPotTransport,524,210.14.71.201] login attempt [bin/alupigus] failed
2013-01-06 05:36:26+0000 [SSHService ssh-userauth on HoneyPotTransport,525,210.14.71.201] login attempt [bin/diana4ever] failed
2013-01-06 05:36:30+0000 [SSHService ssh-userauth on HoneyPotTransport,526,210.14.71.201] login attempt [bin/worlddomination] failed
2013-01-06 05:36:33+0000 [SSHService ssh-userauth on HoneyPotTransport,527,210.14.71.201] login attempt [bin/BUNdAS@#$RT%GQ~EQW#%^QW] failed
2013-01-06 05:36:37+0000 [SSHService ssh-userauth on HoneyPotTransport,528,210.14.71.201] login attempt [kylix/alexxutzu1$@121] failed
2013-01-06 05:36:41+0000 [SSHService ssh-userauth on HoneyPotTransport,529,210.14.71.201] login attempt [mov/masinadescule] failed
2013-01-06 05:36:45+0000 [SSHService ssh-userauth on HoneyPotTransport,530,210.14.71.201] login attempt [be/pufos1234] failed
2013-01-06 05:36:48+0000 [SSHService ssh-userauth on HoneyPotTransport,531,210.14.71.201] login attempt [richard/78274283] failed
2013-01-06 05:36:52+0000 [SSHService ssh-userauth on HoneyPotTransport,532,210.14.71.201] login attempt [root/love123] failed
2013-01-06 05:36:56+0000 [SSHService ssh-userauth on HoneyPotTransport,533,210.14.71.201] login attempt [root/Spm!0you] failed
2013-01-06 05:37:00+0000 [SSHService ssh-userauth on HoneyPotTransport,534,210.14.71.201] login attempt [root/loveandsex4ever] failed
2013-01-06 05:37:03+0000 [SSHService ssh-userauth on HoneyPotTransport,535,210.14.71.201] login attempt [root/freot87bgrtblktgb9mgh5kh] failed
2013-01-06 05:37:09+0000 [SSHService ssh-userauth on HoneyPotTransport,537,210.14.71.201] login attempt [root/=6rj8Icn=O1<Y+&=] failed
2013-01-06 05:37:13+0000 [SSHService ssh-userauth on HoneyPotTransport,538,210.14.71.201] login attempt [root/soledad] failed
2013-01-06 05:37:16+0000 [SSHService ssh-userauth on HoneyPotTransport,539,210.14.71.201] login attempt [root/system9876..] failed
2013-01-06 05:37:20+0000 [SSHService ssh-userauth on HoneyPotTransport,540,210.14.71.201] login attempt [root/cba@horitech##!$] failed
2013-01-06 05:37:24+0000 [SSHService ssh-userauth on HoneyPotTransport,541,210.14.71.201] login attempt [root/shadow@@@ubyta336331jum] failed
2013-01-06 05:37:30+0000 [SSHService ssh-userauth on HoneyPotTransport,542,210.14.71.201] login attempt [root/17tp95] failed
2013-01-06 05:37:34+0000 [SSHService ssh-userauth on HoneyPotTransport,543,210.14.71.201] login attempt [root/72fsd9320] failed
2013-01-06 05:37:38+0000 [SSHService ssh-userauth on HoneyPotTransport,544,210.14.71.201] login attempt [root/sistemas] failed
2013-01-06 05:37:42+0000 [SSHService ssh-userauth on HoneyPotTransport,545,210.14.71.201] login attempt [root/1qazXSW@] failed
2013-01-06 05:37:46+0000 [SSHService ssh-userauth on HoneyPotTransport,546,210.14.71.201] login attempt [root/ahmad750785] failed
2013-01-06 05:37:50+0000 [SSHService ssh-userauth on HoneyPotTransport,547,210.14.71.201] login attempt [root/1q2z3w4x] failed
2013-01-06 05:37:54+0000 [SSHService ssh-userauth on HoneyPotTransport,548,210.14.71.201] login attempt [root/shadow@@@ubyta] failed
2013-01-06 05:37:57+0000 [SSHService ssh-userauth on HoneyPotTransport,549,210.14.71.201] login attempt [root/68N4VpcUgoBFs11TE.] failed
2013-01-06 05:38:01+0000 [SSHService ssh-userauth on HoneyPotTransport,550,210.14.71.201] login attempt [root/mailadmin] failed
2013-01-06 05:38:04+0000 [SSHService ssh-userauth on HoneyPotTransport,551,210.14.71.201] login attempt [root/ktmyzf] failed
2013-01-06 05:38:08+0000 [SSHService ssh-userauth on HoneyPotTransport,552,210.14.71.201] login attempt [root/oracle1] failed
2013-01-06 05:38:12+0000 [SSHService ssh-userauth on HoneyPotTransport,553,210.14.71.201] login attempt [root/NB16hrah55E2.] failed
2013-01-06 05:38:16+0000 [SSHService ssh-userauth on HoneyPotTransport,554,210.14.71.201] login attempt [root/valentinaqwe] failed
2013-01-06 05:38:19+0000 [SSHService ssh-userauth on HoneyPotTransport,555,210.14.71.201] login attempt [root/Sabyn.users.undernet.org] failed
2013-01-06 05:38:23+0000 [SSHService ssh-userauth on HoneyPotTransport,556,210.14.71.201] login attempt [root/ldqsz,bpmcs.] failed
2013-01-06 05:38:31+0000 [SSHService ssh-userauth on HoneyPotTransport,557,210.14.71.201] login attempt [root/b2y3j@my1930] failed
2013-01-06 05:38:35+0000 [SSHService ssh-userauth on HoneyPotTransport,558,210.14.71.201] login attempt [root/egg98<ZsuxG%] failed
2013-01-06 05:38:40+0000 [SSHService ssh-userauth on HoneyPotTransport,559,210.14.71.201] login attempt [root/loler1q] failed
2013-01-06 05:38:43+0000 [SSHService ssh-userauth on HoneyPotTransport,560,210.14.71.201] login attempt [root/n4k4mur41sh3r3] failed
2013-01-06 05:38:47+0000 [SSHService ssh-userauth on HoneyPotTransport,561,210.14.71.201] login attempt [root/gnome-session] failed
2013-01-06 05:38:51+0000 [SSHService ssh-userauth on HoneyPotTransport,562,210.14.71.201] login attempt [root/E9832UIRF2J3IFJ23] failed
2013-01-06 05:38:55+0000 [SSHService ssh-userauth on HoneyPotTransport,563,210.14.71.201] login attempt [root/metiko] failed
2013-01-06 05:39:00+0000 [SSHService ssh-userauth on HoneyPotTransport,564,210.14.71.201] login attempt [root/ilrOm15] failed
2013-01-06 05:39:03+0000 [SSHService ssh-userauth on HoneyPotTransport,565,210.14.71.201] login attempt [root/1111132329993] failed
2013-01-06 05:39:07+0000 [SSHService ssh-userauth on HoneyPotTransport,566,210.14.71.201] login attempt [root/1111132329993aq] failed
2013-01-06 05:39:11+0000 [SSHService ssh-userauth on HoneyPotTransport,567,210.14.71.201] login attempt [root/111111] failed
2013-01-06 05:39:15+0000 [SSHService ssh-userauth on HoneyPotTransport,568,210.14.71.201] login attempt [root/pcservlinux] failed
2013-01-06 05:39:19+0000 [SSHService ssh-userauth on HoneyPotTransport,569,210.14.71.201] login attempt [root/slain22446688] failed
2013-01-06 05:39:22+0000 [SSHService ssh-userauth on HoneyPotTransport,570,210.14.71.201] login attempt [root/server2009] failed
2013-01-06 05:39:26+0000 [SSHService ssh-userauth on HoneyPotTransport,571,210.14.71.201] login attempt [root/coadadebalena] failed
2013-01-06 05:39:30+0000 [SSHService ssh-userauth on HoneyPotTransport,572,210.14.71.201] login attempt [root/muie202020] failed
2013-01-06 05:39:33+0000 [SSHService ssh-userauth on HoneyPotTransport,573,210.14.71.201] login attempt [root/linx123] failed
2013-01-06 05:39:37+0000 [SSHService ssh-userauth on HoneyPotTransport,574,210.14.71.201] login attempt [root/miguelc] failed
2013-01-06 05:39:41+0000 [SSHService ssh-userauth on HoneyPotTransport,575,210.14.71.201] login attempt [root/demined7mc] failed
2013-01-06 05:39:46+0000 [SSHService ssh-userauth on HoneyPotTransport,576,210.14.71.201] login attempt [root/rootpollos] failed
2013-01-06 05:39:49+0000 [SSHService ssh-userauth on HoneyPotTransport,577,210.14.71.201] login attempt [root/215people4477] failed
2013-01-06 05:39:53+0000 [SSHService ssh-userauth on HoneyPotTransport,578,210.14.71.201] login attempt [root/rfhs1229] failed
2013-01-06 05:39:57+0000 [SSHService ssh-userauth on HoneyPotTransport,579,210.14.71.201] login attempt [root/L1n$ux@c@vu#m] failed
2013-01-06 05:40:01+0000 [SSHService ssh-userauth on HoneyPotTransport,580,210.14.71.201] login attempt [root/lam3r3] failed
2013-01-06 05:40:04+0000 [SSHService ssh-userauth on HoneyPotTransport,581,210.14.71.201] login attempt [root/planetbr] failed
2013-01-06 05:40:08+0000 [SSHService ssh-userauth on HoneyPotTransport,582,210.14.71.201] login attempt [root/VHCsoft@admin123] failed
2013-01-06 05:40:12+0000 [SSHService ssh-userauth on HoneyPotTransport,583,210.14.71.201] login attempt [root/tractordelemn] failed
2013-01-06 05:40:16+0000 [SSHService ssh-userauth on HoneyPotTransport,584,210.14.71.201] login attempt [root/dragos3443gff@665$G455454dragos2sd] failed
2013-01-06 05:40:19+0000 [SSHService ssh-userauth on HoneyPotTransport,585,210.14.71.201] login attempt [root/Kr3at0r@I5Th3B3st0F!#$$#!] failed
2013-01-06 05:40:23+0000 [SSHService ssh-userauth on HoneyPotTransport,586,210.14.71.201] login attempt [root/ortega.123#TradeLinuxKi!l|iN6#Th3Ph03$%nix@NdR3b!irD] failed
2013-01-06 05:40:27+0000 [SSHService ssh-userauth on HoneyPotTransport,587,210.14.71.201] login attempt [root/linuxsex123] failed
2013-01-06 05:40:30+0000 [SSHService ssh-userauth on HoneyPotTransport,588,210.14.71.201] login attempt [root/tarenatarena412414] failed
2013-01-06 05:40:34+0000 [SSHService ssh-userauth on HoneyPotTransport,589,210.14.71.201] login attempt [root/qkm@!(%.)=*^&fhE] failed
2013-01-06 05:40:40+0000 [SSHService ssh-userauth on HoneyPotTransport,590,210.14.71.201] login attempt [root/vazador108] failed
2013-01-06 05:40:46+0000 [SSHService ssh-userauth on HoneyPotTransport,591,210.14.71.201] login attempt [root/!#m@mut&#!] failed
2013-01-06 05:40:51+0000 [SSHService ssh-userauth on HoneyPotTransport,592,210.14.71.201] login attempt [root/codecmpeg4codecmpeg4] failed
2013-01-06 05:40:55+0000 [SSHService ssh-userauth on HoneyPotTransport,593,210.14.71.201] login attempt [root/UTCfs2202] failed
2013-01-06 05:40:59+0000 [SSHService ssh-userauth on HoneyPotTransport,594,210.14.71.201] login attempt [root/asroma1927] failed
2013-01-06 05:41:04+0000 [SSHService ssh-userauth on HoneyPotTransport,595,210.14.71.201] login attempt [root/P@ssw0rd] failed
2013-01-06 05:41:09+0000 [SSHService ssh-userauth on HoneyPotTransport,596,210.14.71.201] login attempt [root/ncc1701d] failed
2013-01-06 05:41:12+0000 [SSHService ssh-userauth on HoneyPotTransport,597,210.14.71.201] login attempt [root/welcome1] failed
2013-01-06 05:41:16+0000 [SSHService ssh-userauth on HoneyPotTransport,598,210.14.71.201] login attempt [root/s1rolexcom] failed
2013-01-06 05:41:20+0000 [SSHService ssh-userauth on HoneyPotTransport,599,210.14.71.201] login attempt [root/iamh4ckst4rf0r3ver] failed
2013-01-06 05:41:23+0000 [SSHService ssh-userauth on HoneyPotTransport,600,210.14.71.201] login attempt [root/wvhlyf] failed
2013-01-06 05:41:28+0000 [SSHService ssh-userauth on HoneyPotTransport,601,210.14.71.201] login attempt [root/nti-support] failed
2013-01-06 05:41:32+0000 [SSHService ssh-userauth on HoneyPotTransport,602,210.14.71.201] login attempt [root/sanja123hack] failed
2013-01-06 05:41:36+0000 [SSHService ssh-userauth on HoneyPotTransport,603,210.14.71.201] login attempt [root/zaq12wsx] failed
2013-01-06 05:41:40+0000 [SSHService ssh-userauth on HoneyPotTransport,604,210.14.71.201] login attempt [root/welcome@9] failed
2013-01-06 05:41:43+0000 [SSHService ssh-userauth on HoneyPotTransport,605,210.14.71.201] login attempt [root/clear!@#55896261] failed
2013-01-06 05:41:47+0000 [SSHService ssh-userauth on HoneyPotTransport,606,210.14.71.201] login attempt [root/dltkrhd!240!] failed
2013-01-06 05:41:50+0000 [SSHService ssh-userauth on HoneyPotTransport,607,210.14.71.201] login attempt [root/2010Root1q2w3e] failed
2013-01-06 05:41:57+0000 [SSHService ssh-userauth on HoneyPotTransport,608,210.14.71.201] login attempt [root/Pf0t3nw3g] failed
2013-01-06 05:42:01+0000 [SSHService ssh-userauth on HoneyPotTransport,609,210.14.71.201] login attempt [root/karoca gre!] failed
2013-01-06 05:42:04+0000 [SSHService ssh-userauth on HoneyPotTransport,610,210.14.71.201] login attempt [root/system1234..] failed
2013-01-06 05:42:08+0000 [SSHService ssh-userauth on HoneyPotTransport,611,210.14.71.201] login attempt [root/!msoft1956] failed
2013-01-06 05:42:12+0000 [SSHService ssh-userauth on HoneyPotTransport,612,210.14.71.201] login attempt [root/Lsr4Mny$] failed
2013-01-06 05:42:16+0000 [SSHService ssh-userauth on HoneyPotTransport,613,210.14.71.201] login attempt [root/sercon] failed
2013-01-06 05:42:19+0000 [SSHService ssh-userauth on HoneyPotTransport,614,210.14.71.201] login attempt [root/!you#ming%shun&] failed
2013-01-06 05:42:23+0000 [SSHService ssh-userauth on HoneyPotTransport,615,210.14.71.201] login attempt [root/R3lisysfanta] failed
2013-01-06 06:03:38+0000 [SSHService ssh-userauth on HoneyPotTransport,617,64.191.21.190] login attempt [173.252.237.117/cacutza] failed
2013-01-06 06:03:39+0000 [SSHService ssh-userauth on HoneyPotTransport,617,64.191.21.190] login attempt [173.252.237.117/173.252.237.115] failed
2013-01-06 07:58:11+0000 [SSHService ssh-userauth on HoneyPotTransport,618,64.191.21.190] login attempt [173.252.237.118/cacutza] failed
2013-01-06 07:58:12+0000 [SSHService ssh-userauth on HoneyPotTransport,618,64.191.21.190] login attempt [173.252.237.118/173.252.237.119] failed
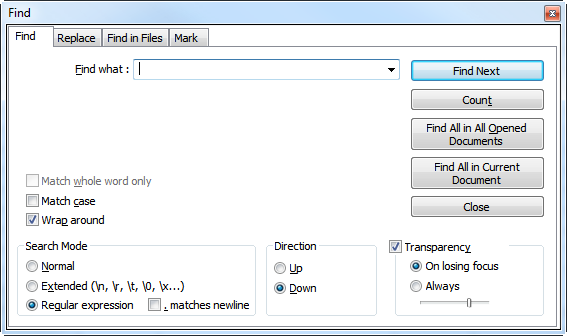
Now lets say we just wanted the passwords from this log. As this is just a small sampling, you can imagine doing this manually would not be a fun task. Luckily, Notepad++ has a solution for this. Open Notepad++ and paste the logs I put above in if you would like to follow along. With Notepad++ open, hit ctrl+f to bring up the search function.
The Find function has a lot of options. We will start in the Find Tab for now, and then move to the Replace. By having the Regular expression radio button selected in the bottom left we are telling Notepad++ we will be using Regex. There are some other options but we will focus on this for now.
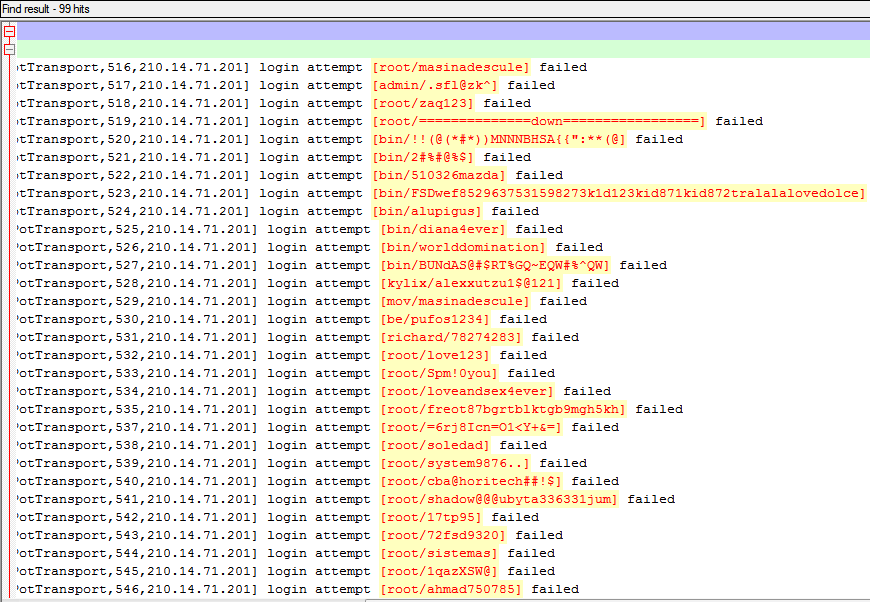
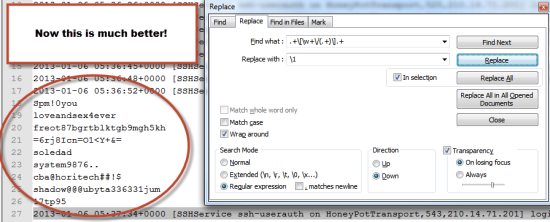
Looking at the log, we can quickly identify where the password is. The username and password are always between [] and always separated by a /. The Regex for what I just described is this:
To break it down for you we are looking for "[" which is the "\[", then we are looking for any number of word characters which is covered by "\w+", then a "/" which is covered with "\/", then any number of any characters which is covered by ".+" and lastly a "]" which is covered by "\]".
Now with that regex in the find box click find all in current document which should give you something like this:
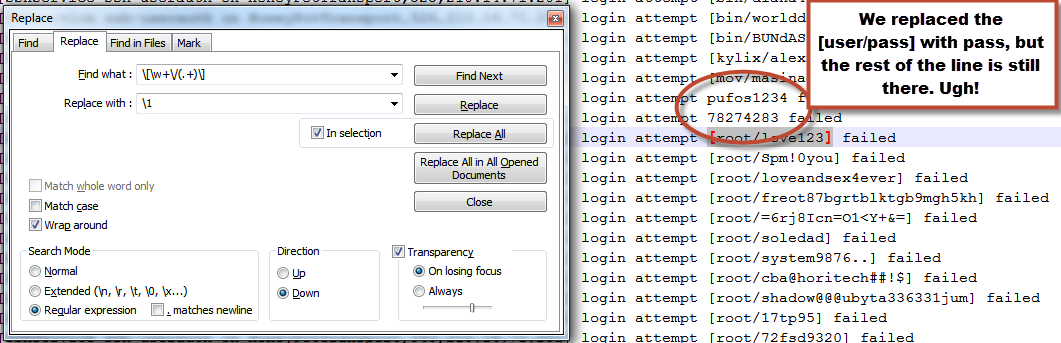
Great! Now we have a regex string that matches what we are looking for, but how do you get the data out of that log? That is what I had a little trouble with at first. I feel like I should be able to ctrl+c and ctrl+v like there is no tomorrow, but that is not the case. We have to instead use the replace feature. That is why we need to wrap () around where the password is in our regex. So lets switch to the replace tab, and add our modified regex which should now look like this:
Now add \1 to the replace field. What this means is replace with the pattern specified in the first set of (), in our case (.+) which is where the password is in the pattern. Now hit replace a couple times to see what it is doing. So as you can probably tell, we are closer to what we want but not quite there. This is replacing the [username/password] with password but the rest of the line is still there.
I know what you are saying at this point, "Dang 1aN0rmus, why should I bother I could probably have done this manually by now". I understand your frustration, but trust me, after you do this a few times you'll be eating up logs like it's no ones business. Don't fret, we will get through this.
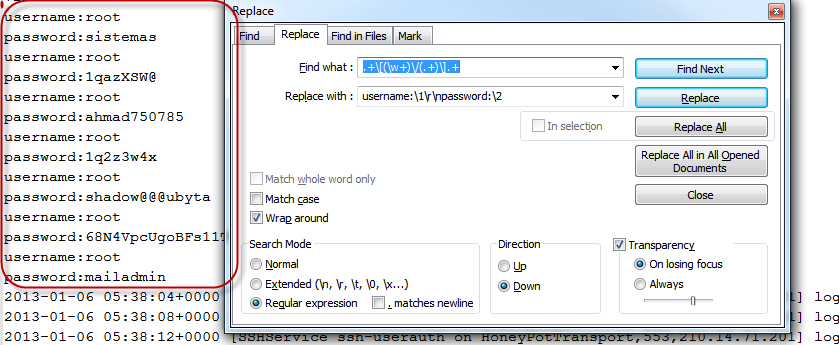
So, how do we get the rest of the line? It's very simple, we just have to build a regex that will capture the entire line but pull out what we need. This is easier than you are thinking. This can almost always be done by adding a ".+" before and after the regex string you already built. Giving us the following:
Now we can when we hit replace lets see what happens.
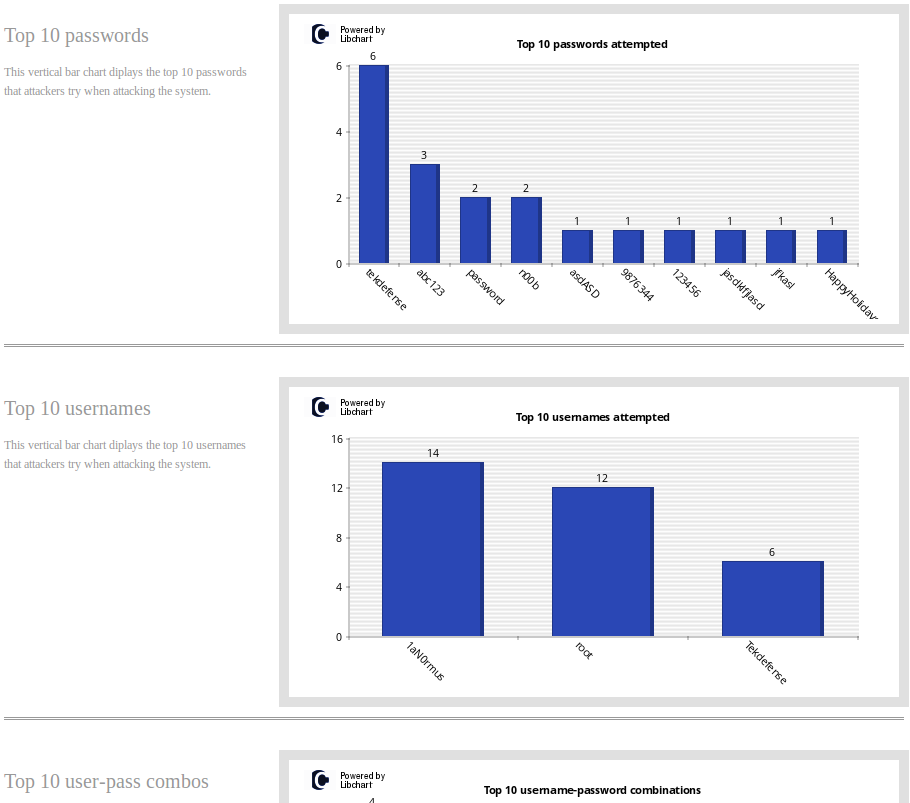
Perfect! Just what we wanted. Click Replace All and you are done. The file is perfectly formatted for Pipal
This methodology will help you tremendously, but remember you will need to change up your regex and even your replacement text to fit each new situation. This will work fin for pulling passwords from all Kippo logs, but if your mission changes and you would like usernames and passwords you would need to modify this to suit your needs. Hopefully you have the tools to accomplish this now though.
 Tuesday, January 22, 2013 at 9:43AM
Tuesday, January 22, 2013 at 9:43AM  Admin |
Admin |  Post a Comment |
Post a Comment |  Honeydrive,
Honeydrive,  Kippo,
Kippo,  honeypot,
honeypot,  ssh in
ssh in  News
News