Tuesday
Dec042012
Are you feeling lucky?
 Tuesday, December 4, 2012 at 5:06PM
Tuesday, December 4, 2012 at 5:06PM Today something happened that I thought was nearly impossible. Gmail spam filters failed me, letting a culprit slip through to my inbox. Not only did Gmail let this spam through but it had the audacity to mark it as an important message. What is this world coming to?
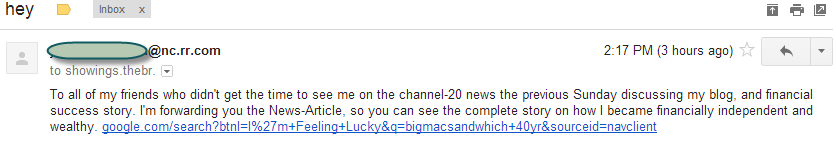 In all seriousness, as good as Google and the other mail providers are, no technology is perfect. At this point you are probably reading this and thinking I should be a nominee for Defcon's Captain Obvious award. I assure you, while not unique, this is at least a hipster class attack. What I thought was interesting in this one was the link, but before getting into that, here are the details of the email for those who are interested.
In all seriousness, as good as Google and the other mail providers are, no technology is perfect. At this point you are probably reading this and thinking I should be a nominee for Defcon's Captain Obvious award. I assure you, while not unique, this is at least a hipster class attack. What I thought was interesting in this one was the link, but before getting into that, here are the details of the email for those who are interested.*changed addresses to protect the innocent*Delivered-To: mygmailaccount@gmail.comReceived: by 10.58.230.3 with SMTP id su3csp41229vec;Tue, 4 Dec 2012 11:17:34 -0800 (PST)Received: by 10.58.172.103 with SMTP id bb7mr12819169vec.41.1354648653873;Tue, 04 Dec 2012 11:17:33 -0800 (PST)Return-Path: <somerandomdude@nc.rr.com>Received: from cdptpa-omtalb.mail.rr.com (cdptpa-omtalb.mail.rr.com. [75.180.132.120])by mx.google.com with ESMTP id jd5si1502108vcb.68.2012.12.04.11.17.33;Tue, 04 Dec 2012 11:17:33 -0800 (PST)Received-SPF: pass (google.com: domain of somerandomdude@nc.rr.com designates 75.180.132.120 as permitted sender) client-ip=75.180.132.120;Authentication-Results: mx.google.com; spf=pass (google.com: domain of somerandomdude@nc.rr.com designates 75.180.132.120 as permitted sender) smtp.mail=somerandomdude@nc.rr.comReturn-Path: <somerandomdude@nc.rr.com>Authentication-Results: cdptpa-omtalb.mail.rr.com smtp.user=somerandomdude@nc.rr.com; auth=pass (LOGIN)X-Authority-Analysis: v=2.0 cv=b+UwE66x c=1 sm=0 a=05ChyHeVI94A:10 a=IkcTkHD0fZMA:10 a=ayC55rCoAAAA:8 a=1XWaLZrsAAAA:8 a=wzPgKpAVP4n484FzqIcA:9 a=QEXdDO2ut3YA:10 a=u6pmmePcEMEA:10 a=0EOytqNtNh4q28ximZfgKQ==:117X-Cloudmark-Score: 0X-Authenticated-User: somerandomdude@nc.rr.comReceived: from [10.127.132.168] ([10.127.132.168:34037] helo=cdptpa-web17-z02)by cdptpa-oedge02.mail.rr.com (envelope-from <somerandomdude@nc.rr.com>)(ecelerity 2.2.3.46 r()) with ESMTPAid 4C/96-00778-B4C4EB05; Tue, 04 Dec 2012 19:17:31 +0000Message-ID: <20121204191731.ZJV9L.107832.root@cdptpa-web17-z02>Date: Tue, 4 Dec 2012 14:17:31 -0500From: <somerandomdude@nc.rr.com>To: showings.thebremnergroup@gmail.comSubject: heyMIME-Version: 1.0Content-Type: text/plain; charset=utf-8Content-Transfer-Encoding: 7bitX-Priority: 3 (Normal)Sensitivity: NormalX-Originating-IP:
Okay, now that you have that out of your system, back to what I think is somewhat unique. I should preface this by saying that this is probably not the first time this technique has been used, but it is the first time I have seen it.
As you savvy readers have probably already noticed the link is:
google.com/search?btnI=I%27m+Feeling+Lucky&q=bigmacsandwhich+40yr&sourceid=navclient
So like every phishing email, this one wants us to click the link to view malicious content. This is usually done by:
1. hiding the link using html in the email
<a href="malicioussiteisbad.com">TotallyLegitSite.com</a>
2. using a url shortner
bit.ly/1amn0tbad
3. or using a url that seems legitimate'ish.
mail.tekdefense.com.co.uk.ws.tk
This attacker instead did something a little bit more clever. Using a particular query string in the Google URI the attacker utilizes the "I'm Feeling Lucky" feature of Google to give them a link that seemingly goes to Google, but instead is a redirect to a malicious site. For those of you who aren't aware, the "I'm Feeling Lucky" feature is a Google search option will bring the user directly to the first result for a specific search query.
In the case of the email I recieved the query is for "bigmacsandwhich" and "40yr". The first result for this is a page set to redirect through a few other sites until you reach the final destination where the bad stuff is set to happen.
The final landing site is http://cnbc-20news(.)net/blamom23.htm. This is of course a fake version of a CNBC site with a somewhat legitimate looking URL promoting a work from home program.
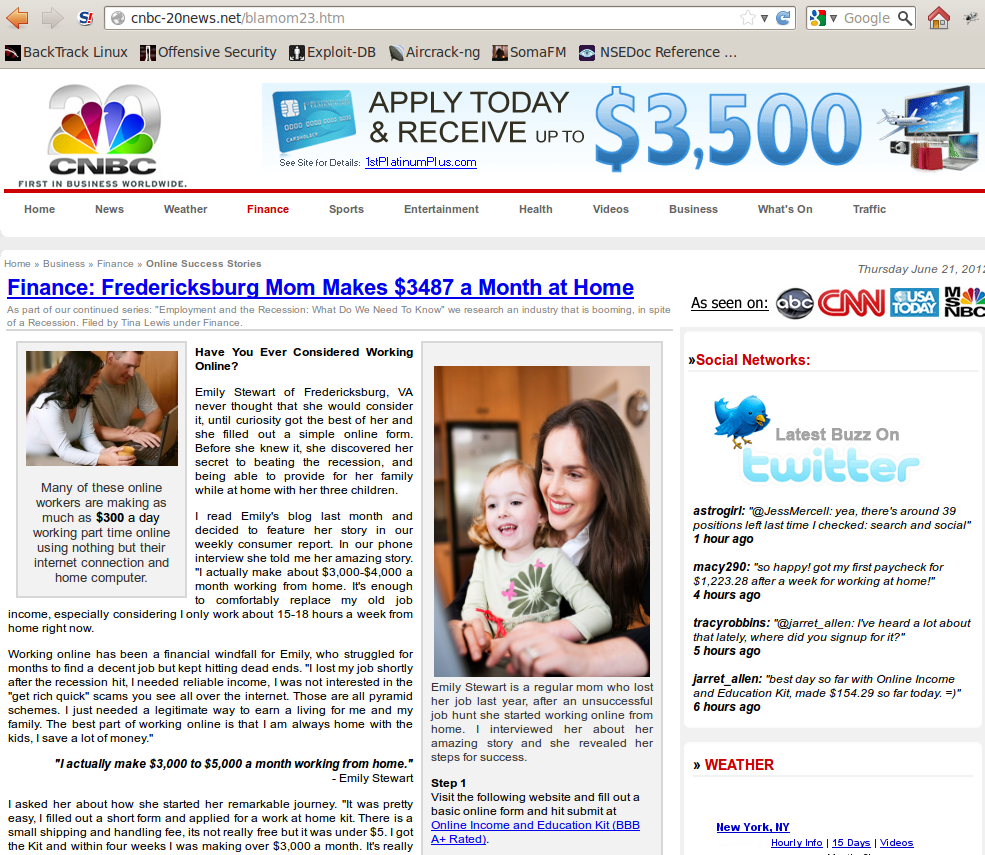
I checked the URL with Virustotal which showed clean. Looking at the source I saw that almost every link went to a specific URL (http://cnbc-20news(.)net/article2592au2b.php). This link of course redirects us again leading us to http://www.leadinghomeincome(.)com/?aid=44&sid=&sid2=&sid3=&. This is your typical "lets make a deal now on this exciting offer" site. Good thing I had NoScript running or leaving that would have been a nightmare with all the popups and "are you sure you want to leave?" messages. Now I wish this got more exciting with perhaps a drive-bye malware attempt, but nope. All seems to end there. To make sure I ran the URLs through my Cuckoo instance to see if anything out of the normal occurred. Seems all of this for click fraud and a work from home scam.
How sustainable is this technique though, and I am referring specifically to the Google "I'm feeling lucky" trick. In order for this to work an attacker needs to get his/her site or a site that was compromised to be the first for some query in Google. I'm not an SEO expert so its hard for me to say how easy or not this is. I am not sure even if it isn't too bad to setup, is it worth the extra time verse the normal methods?
What do you guys and gals think? Let me know.
 Admin |
Admin |  2 Comments |
2 Comments | tagged  Feeling Lucky,
Feeling Lucky,  click fraud,
click fraud,  email,
email,  gmail,
gmail,  mail,
mail,  phishing,
phishing,  scan in
scan in  News
News
 Feeling Lucky,
Feeling Lucky,  click fraud,
click fraud,  email,
email,  gmail,
gmail,  mail,
mail,  phishing,
phishing,  scan in
scan in  News
News