Automater 1.0 - Passive IP and URL Analysis
 Sunday, November 25, 2012 at 2:33PM
Sunday, November 25, 2012 at 2:33PM wget https://github.com/1aN0rmus/TekDefense/archive/master.tar.gz
tar -xvcf master.tar.gz
cd TekDefense-masterchmod +x *
./Automater.py -h
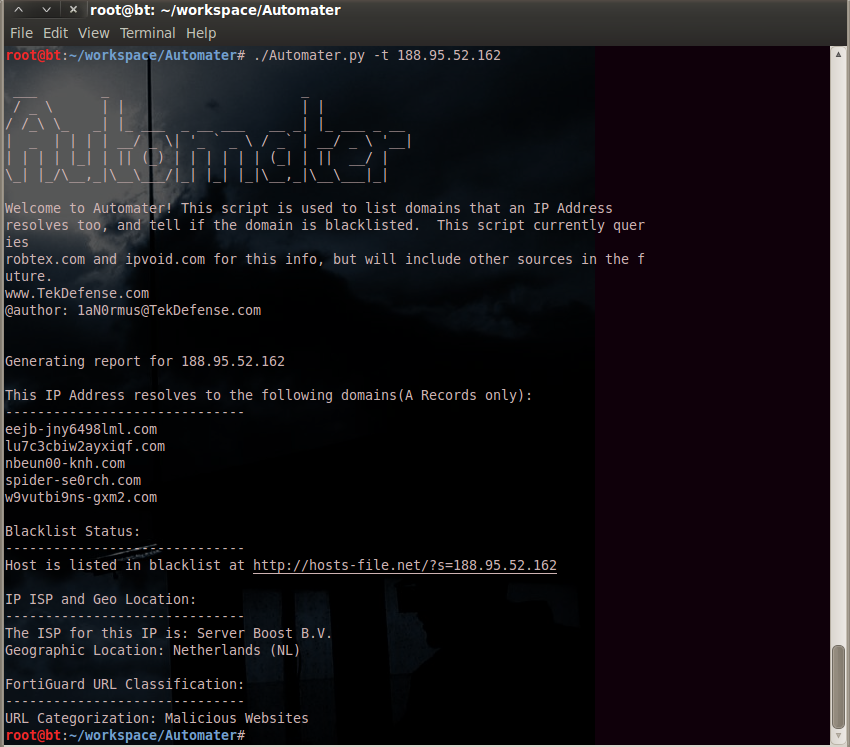
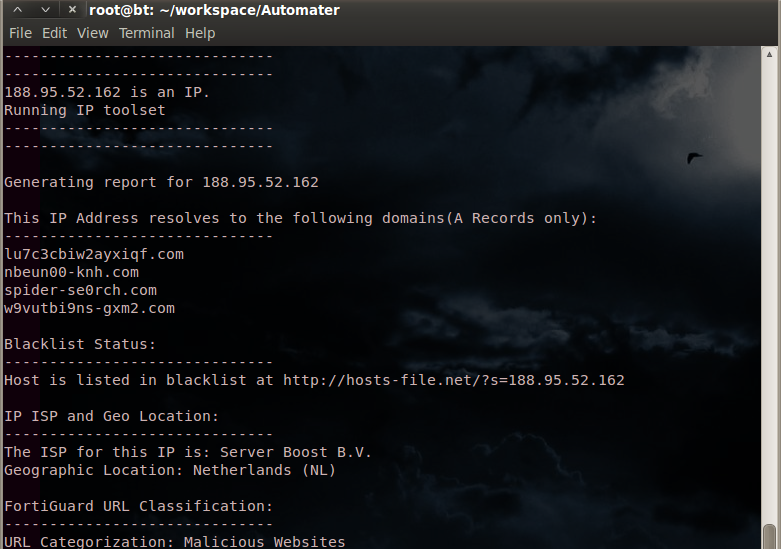
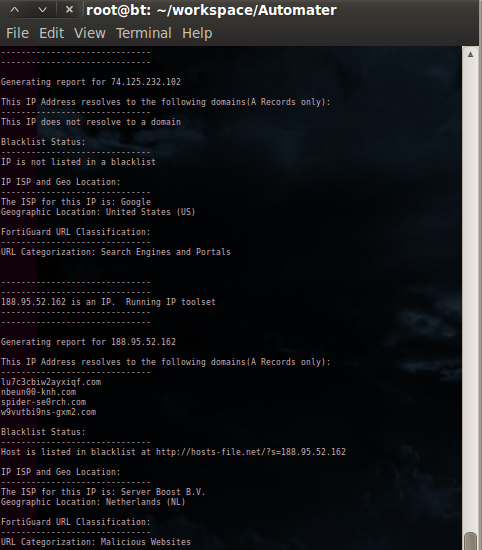
./Automater.py -t 188.95.52.162
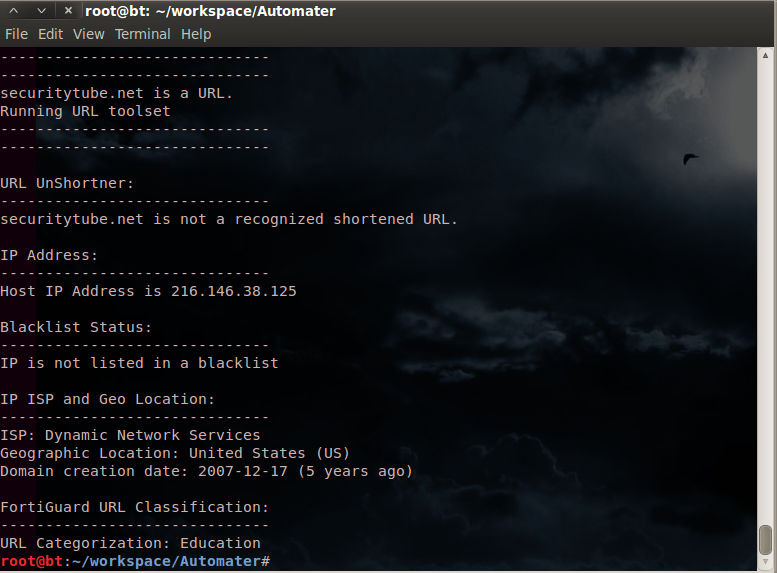
./Automater.py -t securitytube.net
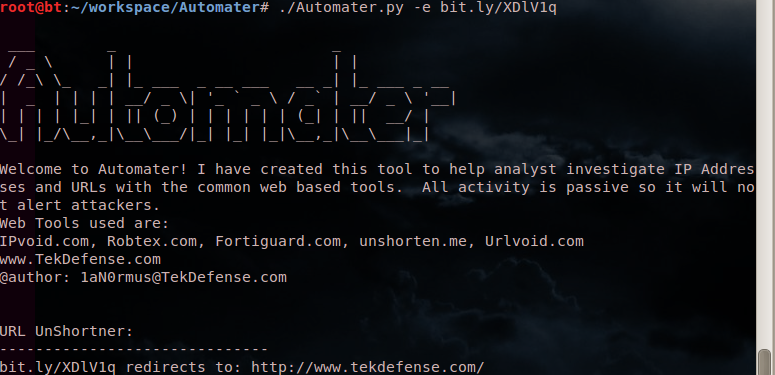
./Automater.py -e bit.ly/XDlV1q
./Automater.py -f hostsss
./Automater.py -f hostsss -o host.out
- If the IP or URL has not been previously scanned at IPVoid or URLVoid, the script is supposed to submit the IP or URL and then pull results. This seems to work most of the time, but on occasion it will not wait long enough to pull the appropriate result. Running the command a second time will work though.
- Can not use the -e and -f switch together.
- URLs with http:// cannot be scanned. Must take the http:// out for it to work.
- Please submit any other bugs to 1aN0rmus@tekdefense.com
Upcoming Features:
- For those who would like to be able to just query a specific engine or source such as robtex, we will be creating an option to do so.
- Check IP and/or URL against Malwaredomainlist
- Check IP and/or URL against malware sandboxes such as ThreatExpert.
- Summary report that will give statistics on the targets highlighting the known bad information such as blacklists and malicious URL categories.
- Please submit feature requests to 1aN0rmus@tekdefense.com