Automater - IP and URL analysis tool
 Sunday, November 4, 2012 at 11:35AM
Sunday, November 4, 2012 at 11:35AM Update: Automater gets its own project page http://www.tekdefense.com/automater/
One challenge I have faced, as well as seen other analyst face as well is the amount of time it takes to investigate an IP Address or URL. If you are like most analyst you have probably used at least some if not all of the following web tools to investigate IPs or URLs involved in an incident:
As I mentioned previously to lookup an IP against all or even some of these takes more time than it should. Additionally, as they all are formatted differently and have different options, you can not export them in a format that can be attached to a trouble ticket, evidence file, or even an email. Noticing this issue, I attempted to fix it by creating a python program that will scrape the previously mentioned resources to pull out the information relevant to what the analyst needs.
Meet Automater:
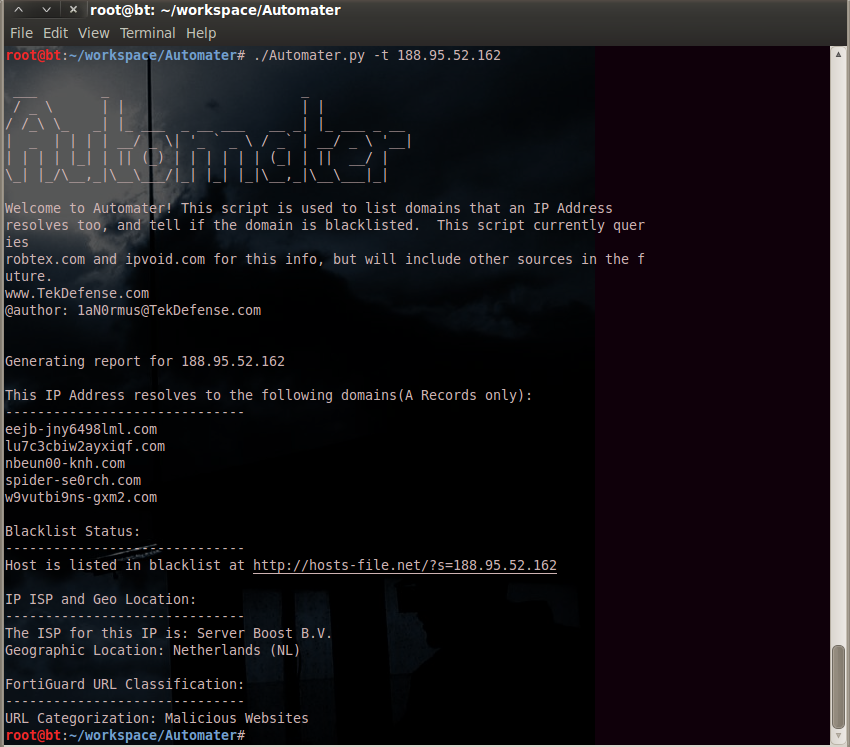
The tool currently only queries IPVoid, Robtex, and Fortiguard currently, but I am working on adding modules from all the resources I mentioned earlier in the article. The help option will explain where I am heading with the project, all though I am not quite there yet.
root@bt:~/workspace/Automater# ./Automater.py -hONLY -t AND -h WORK CURRENTLY!!-t: target ip or url. URL must include http://-s: source engine (robtex, ipvoid, fortiguard)-a: all engines-h: help-f: import a file of IPs and/or URLs-o: output results to file-i: Interactive ModeExamples:./Automater.py -t 123.123.123.123 -a -o result.txt./Automater.py -f hosts.txt -s robtex -o results.txt
Automater right now only takes the -t and the -h options and only works for one target at a time. This again will change as I modify it. URL support has not been added yet either.
I am posting this now in its pre-release form because I would like to hear from the community what types of features they would like to see added. I would also like to know of any bugs you can find. Lastly, I am of course interested in anyone who would like to contribute to the project. If all goes as planned I would like to have the tool fully functional within a couple of weeks. Once complete I will attempt to pitch the tool to Doug Burks to add to his Security Onion Distro. I think this could be a really nice tool for analysts.
Contribute to, or download the tool on Github.
Report any Bugs or feature requests to 1aN0rmus@TekDefense.com
DEMO:
 Admin |
Admin |  Post a Comment |
Post a Comment |  1aNormus,
1aNormus,  Automater,
Automater,  URL Filtering,
URL Filtering,  analysis,
analysis,  blacklist,
blacklist,  intrusion analysis,
intrusion analysis,  investigation,
investigation,  ipvoid,
ipvoid,  python,
python,  robtex,
robtex,  tekdefense,
tekdefense,  tektip in
tektip in  News,
News,  TekTip
TekTip